
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
SHA−3 (Secure Hash Algorithm 3)
The new model of the technique for information security is referred to as SHA-3. This is a piece of code that encrypts the information and makes it unreadable by anyone with out a key. The fundamental capabilities in preceding versions referred to as SHA-1 and SHA-2 vary from SHA-3.
SHA-3 is a part of a bigger group of secret code tools called Keccak. This group was created by a team of people named Guido Bertoni, Joan Daemen, Michael Peeters, and Gilles Van Assche, who built upon something called RadioGatun. They made Keccak do more things, like making secret codes for messages and keeping information safe while sending it over the internet.
Keccak works in a unique way called sponge construction. It's like a sponge that can soak up any amount of water (or data) and squeeze out any amount too. It can mix up the data so no one can understand it without the key. This makes it very flexible and useful.
The older algorithms, SHA-1 and SHA-2, are still in use even though SHA-3 is relatively new. But if needed, SHA-3 can replace them directly. The goal of SHA-3 is to make the secret codes stronger and better overall.
For small messages, there's a faster version called KangarooTwelve. It works quicker for short messages and has special settings to make it work better.
The SHA-3 family has six hash functions with digests (hash values) of 128, 224, 256, 384, or 512 bits: SHA3-224, SHA3-256, SHA3-384, SHA3-512, SHAKE128, and SHAKE256.
This library is compatible with every algorithm listed above.
- SHA3-224, 28 bit Digest-Size
- SHA3-256, 32 bit Digest-Size
- SHA3-384, 48 bit Digest-Size
- SHA3-512, 64 bit Digest-Size
- SHAKE-128
- SHAKE-256
History of SHA-3
The Keccak algorithm is based on earlier algorithms called PANAMA and RadioGatun and was developed by Guido Bertoni, Joan Daemen, Michael Peeters, and Gilles Van Assche. Daemen and Craig Clapp created PANAMA in 1998. Later, in 2006, Daemen, Peeters, and Van Assche presented RadioGatun, an upgraded version of PANAMA.
The National Institute of Standards and Technology (NIST) released a competition in 2006 to expand SHA-3, a new wellknown for secret codes. Previous secret algorithms like MD5, SHA-0, and SHA-1 were no more secure, so this become done to offer an opportunity to SHA-2.
Keccak was one of the competition's fifty-one entries. It advanced to the final round in December 2010 after going through several testing and improvement rounds. Keccak was modified during the competition to increase its strength and security.
On October 2, 2012, Keccak was chosen as the competition's support. NIST published a draft of the FIPS 202 "SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions" in 2014. This draft was approved on August 5, 2015, creating SHA-3 an official hashing standard.
Design of SHA-3
The SHA-3 design uses a method known as sponge construction. Here's how it works −
- Absorption Phase − During this step, the "sponge" absorbs information. A transformation function called f is used to combine each block of data with a portion of the sponge's current state. This function rearranges the state's components. The "rate" refers to how much of the state interacts with the input/output, whereas the "capacity" refers to the extent of the state that remains constant. The system's security depends on its capability.
- Squeeze Phase − During the squeeze phase, the transformation function f alternates between reading output blocks from the same subset of the state. To modify the length of the output, change the function's parameters.
The internal state of SHA-3 is a grid of words, each with a set number of bits. The size of this grid influences the algorithm's overall security. Variable versions of SHA-3 allow for different output lengths and word sizes, making it suitable to a wide range of security needs.
Some SHA-3 examples, like SHA3-224, SHA3-256, SHA3-384, and SHA3-512, have output lengths less than the rate, therefore no extra transformations are necessary during the squeezing phase. However, with versions like SHAKE128 and SHAKE256, which allow for different output lengths, more changes are required to produce the desired outcome.
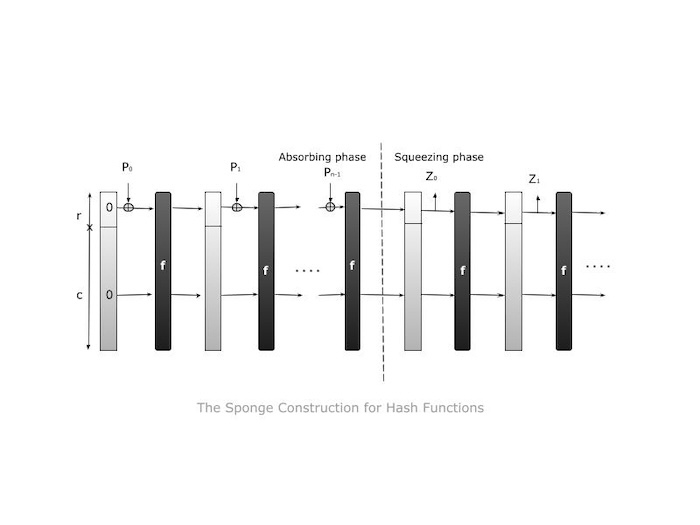
Here is an overview of how sponge construction works −
- The input string N is padded with a function named pad. This ensures that the length of the padded string P is divisible by the rate r, which is represented by len(P)/r = n, where len(P) is P's length.
- The padded string P is then separated into n successive blocks, each containing r bits. These blocks are identified as P0, P1,..., and Pn-1.
- The state S is initialised as a string of b zero bits, where b is the overall width of the state.
- Each block Pi is extended at the end with a string of c zero bits, where c equals b - r. This creates a block with length b. Then, this expanded block is XORed with the current state S. Following that, a block permutation function f is applied to the result to generate a new state S.
- The output string Z is set to an empty string. While Z's length is less than d (the desired output length), the first r bits of the current state S are added to Z. If Z is still less than d bits, f is applied to S again to generate a new state S. This operation will continue until Z reaches the desired length d.
- Finally, if Z is longer than d bits, it is truncated to get the final result.
In SHA-3, the internal state S is defined as a 5 × 5 grid of words, each w bits wide. In SHA-3, w is set to 64, giving a total state size of 1600 bits (5 × 5 × 64 = 1600).
But Keccak allows for various word sizes, starting with w = 1 bit, which gives a total state size of 25 bits. The flexibility in word size enables the testing of cryptanalytic attacks with smaller state sizes, as well as realistic implementations with intermediate state sizes ranging from w = 8 (200 bits) to w = 32 (800 bits).
In some SHA-3 implementations, like SHA3-224, SHA3-256, SHA3-384, and SHA3-512, the rate r (the portion of the state used to absorb input) is greater then the desired result length d. In these cases, no further block permutations need to be made during the squeezing step. Rather, the state's leading d bits give the desired hash output.
SHAKE128 and SHAKE256, on the other hand, allow for arbitrary output lengths. This capability is useful in applications like optimal asymmetric encryption padding, where the output length has to be customised to meet specific requirements.
Examples of SHA-3 variants
Suppose we have a pleaintext as "Tutorialspoint" so the hash values accoring to the SHA-3 variants are as follows −
SHA3-224
This variant produces a 224-bit hash value. Hash value for "Tutorialspoint" - b3b059b134b17b4bed361b16392b40b16648695eabbf87896c0f8e50
SHA3-256
This variant produces a 256-bit hash value. Hash value for "Tutorialspoint" - a789f0a2eb3b13ec69245210b8c522bbb7c33ccb0561729697294bcd35367622
SHA3-384
This variant produces a 384-bit hash value. Hash value for "Tutorialspoint" - 68ccee414159dc755f8aa17d82bd1958c956cd09ecf9a221b661c93ce7b36e40237 cbadddf48a0600e1eda4ecdd87295
SHA3-512
This variant produces a 512-bit hash value. Hash value for "Tutorialspoint" - fb3e821c3a16c720f1137673c6d4247f26e88889093831cf4ca2bb1ef7e0ce45667 98297d891b5fae396e93fe4b7003be794e18a194e438a1c802798d0703819
SHAKE128
Hash value: 42a52efbca7de46de5ab54b443870c48
SHAKE256
Hash value 06c9b7ff87b0d9360f0a2e0d2fe58757945f79b8d7b5e7a2a14827c8d37ff570
These variants provide different levels of security and output lengths to suit various cryptographic needs. The above hash values are unique representations of the plaintext "Tutorialspoint" using different SHA-3 variants.
Additionally, there are also SHAKE128 and SHAKE256, which allow for arbitrary output lengths, making them suitable for applications requiring flexible hash lengths.
Comparison of Various SHA Functions
| Function | Output Size | Security | Usage |
|---|---|---|---|
| SHA-1 | 160 bits | Vulnerable to collision attacks, no longer considered secure | Legacy systems, but should be avoided for new designs |
| SHA-2 (SHA-224, SHA-256, SHA-384, SHA-512) | 224, 256, 384, and 512 bits respectively | Generally considered secure and it is resistant to collision attacks | Data integrity verification, digital signatures, cryptographic applications |
| SHA-3 (SHA3-224, SHA3-256, SHA3-384, SHA3-512) | 224, 256, 384, and 512 bits respectively | Designed to provide security against known cryptographic attacks | Alternative to SHA-2, new designs requiring cryptographic hashing |
| SHAKE128 and SHAKE256 | Variable (can produce hash values of any desired length) | Designed to provide security similar to SHA-3 | Flexible hash lengths required, cryptographic protocols needing dynamic hash length |
Implementations of SHA-3 using Python
The code for Python calculates the SHA-3 hash values of a given message at various hash lengths (224, 256, 384, and 512 bits). So we will use Python's hashlib package whichprovides secure hashing and message digest methods. It contains implementations for various cryptographic hash methods, likeSHA-3. It checks if the length is 224, 256, 384, or 512 bits, and then computes the hash using the correct hashlib.sha3_224(), hashlib.sha3_256(), hashlib.sha3_384(), or hashlib.sha3_512() function. So the Python code for various SHA-3 variants is as follows −
import hashlib
def sha3(message, length):
if length == 224:
return hashlib.sha3_224(message.encode()).hexdigest()
elif length == 256:
return hashlib.sha3_256(message.encode()).hexdigest()
elif length == 384:
return hashlib.sha3_384(message.encode()).hexdigest()
elif length == 512:
return hashlib.sha3_512(message.encode()).hexdigest()
else:
return "Invalid length"
message = "Tutorialspoint"
print("SHA3-224 hash:", sha3(message, 224))
print("SHA3-256 hash:", sha3(message, 256))
print("SHA3-384 hash:", sha3(message, 384))
print("SHA3-512 hash:", sha3(message, 512))
Output
SHA3-224 hash: b3b059b134b17b4bed361b16392b40b16648695eabbf87896c0f8e50 SHA3-256 hash: a789f0a2eb3b13ec69245210b8c522bbb7c33ccb0561729697294bcd35367622 SHA3-384 hash: 68ccee414159dc755f8aa17d82bd1958c956cd09ecf9a221b661c93ce7b36e40237cbadddf48a0600e1eda4ecdd87295 SHA3-512 hash: fb3e821c3a16c720f1137673c6d4247f26e88889093831cf4ca2bb1ef7e0ce4566798297d891b5fae396e93fe4b7003be794e18a194e438a1c802798d0703819
Implementations of SHA-3 using Java
To implement the SHA-3 variants we will use bulit-in classes on Java - java.security.MessageDigest and java.security.NoSuchAlgorithmException. The MessageDigest class is used for cryptographic hash functions. It offers algorithms like SHA-3 for secure hashing. The code shows how to compute SHA-3 hash values for the given message of different lengths using Java's MessageDigest class. It changes the hash bytes to hexadecimal representation. So the code for SHA-3 in Java is as follows −
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
public class Sha3Algorithm {
public static String sha3(String msg, int length) throws NoSuchAlgorithmException {
MessageDigest digest = MessageDigest.getInstance("SHA3-" + length);
byte[] hashBytes = digest.digest(msg.getBytes());
StringBuilder hexString = new StringBuilder();
for (byte hashByte : hashBytes) {
String hex = Integer.toHexString(0xff & hashByte);
if (hex.length() == 1) hexString.append('0');
hexString.append(hex);
}
return hexString.toString();
}
public static void main(String[] args) throws NoSuchAlgorithmException {
String msg = "Tutorialspoint";
System.out.println("SHA3-224 hash: " + sha3(msg, 224));
System.out.println("SHA3-256 hash: " + sha3(msg, 256));
System.out.println("SHA3-384 hash: " + sha3(msg, 384));
System.out.println("SHA3-512 hash: " + sha3(msg, 512));
}
}
Output
SHA3-224 hash: b3b059b134b17b4bed361b16392b40b16648695eabbf87896c0f8e50 SHA3-256 hash: a789f0a2eb3b13ec69245210b8c522bbb7c33ccb0561729697294bcd35367622 SHA3-384 hash: 68ccee414159dc755f8aa17d82bd1958c956cd09ecf9a221b661c93ce7b36e40237cbadddf48a0600e1eda4ecdd87295 SHA3-512 hash: fb3e821c3a16c720f1137673c6d4247f26e88889093831cf4ca2bb1ef7e0ce4566798297d891b5fae396e93fe4b7003be794e18a194e438a1c802798d0703819