
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - AES Key Expansion Algorithm
For use in AES encryption, a single initial key can be expanded into a series of round keys using the AES (Advanced Encryption Standard) key expansion technique. These round keys are needed for each round of AES encryption and decryption.
The AES key expansion method receives a four-word (16-byte) key and returns a linear array of 44 words (176 bytes). This is sufficient to provide both the initial AddRoundKey step and a four-word round key for each of the cipher's ten rounds.
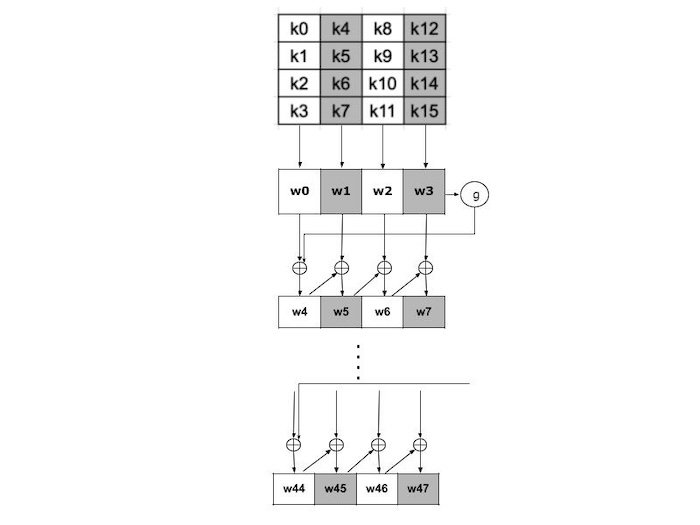
How algorithm works?
In simple terms, the AES key expansion algorithm functions as follows −
- Initial Key − The algorithm makes use of an initial key. Depending on the level of security needed, this key's length can range from 128 to 256 bits.
- Round Constants − The approach makes use of a set of round constants, which are predefined values used in the key expansion process.
- Word Size − The key divides words into individual blocks. A word typically has 32 bits in it. For example, four 32-bit words are created from a 128-bit key.
- Key Schedule − The term "key schedule" refers to a set of round keys generated using the key expansion process. The initial round key and the extra round keys that were derived from it are both included in this schedule.
- Expansion Rounds − The algorithm performs several tasks in each expansion round, such as −
- RotWord − This function rotates the bytes in a word.
- SubWord − Applyes a substitution operation using a predetermined S-box.
- Rcon − XORs the word using a round constant.
- Round Keys − The order of round keys that are still in place following all expansion rounds defines the key schedule. Each round key is used in the corresponding round of AES encryption or decryption.
Overall, the key expansion method increases security and prevents cryptographic attacks by ensuring that each AES encryption and decryption round has a unique round key.
Mathematical Representation
Let us denote −
- K is the first key, having N bits in its length.
- The word count (Nk) of the key is its total word count (e.g., 4 for a 128-bit key, 6 for a 192-bit key, and 8 for a 256-bit key).
- Nr, the AES round identifier, is 10 for AES-128, 12 for AES-192, and 14 for AES-256.
Key Expansion Process
- Step 1: Make the round keys first. Establish the first word K in a word array W. Iterate to generate (Nr + 1) round keys −
for i = N_k to (4 * (N_r + 1) - 1):
if i mod N_k == 0:
temp = RotWord(W[i-1]) ^ SubWord(W[i-1]) ^ Rcon(i / N_k)
else:
temp = W[i-1] ^ W[i-N_k]
W[i] = temp
- Step 2: Finalize Round Keys: After the loop, the array W has all round keys.
Notations
- RotWord(w) − Rotate the word w's bytes in a manner that is cyclic.
- SubWord(w) − Use the AES S-box to swap out each byte in the word w.
- Rcon(i) − Produce the current round's i 's round constant, or Rcon.
Compute the Round Constant Rcon
The round constant for the i-th round can be found by computing Rcon(i)=(RC[i],0,0,0), where RC[i] is the i-th element of the round constant array.
This representation provides a mathematical description of how the original key is transformed into a set of round keys used in AES encryption and decoding.
Example of AES Key Expansion
Now we are going to discuss the AES (Advanced Encryption Standard) key expansion algorithm with an example. For this example, we will be using AES-128, so our initial key will be 128 bits (16 bytes).
The first key can be considered as a set of bytes −
2b 7e 15 16 28 ae d2 a6 ab f7 97 66 76 15 13 1
This key is 128 bits long.
Let's look at every step of the key expansion process −
Initial Key
2b 7e 15 16 28 ae d2 a6 ab f7 97 66 76 15 13 1
Expansion Rounds
We start by adding the first key to our list of round keys. Following that, we iteratively generate more round keys until we reach a total of 11.
Round 1
In the RotWord, SubWord, and XOR operations, we use the round constant −
RotWord: 7e 15 16 2b SubWord: 63 cb e7 8c Rcon: 01 00 00 00 Round 1 Key: 63 cb e7 8c 09 cf 4f 3c 3b a9 82 fb 11 13 d8 2c
Round 2
The word from the previous round key is XORed four positions back −
Round 2 Key: a0 fa fe 17 88 54 2c b1 23 a3 39 39 2a 6c 76 05
Subsequent Rounds
Round keys are generated in this way until a total of 11 keys have been generated.
Final Round Keys
Round 0 (Initial Key): 2b 7e 15 16 28 ae d2 a6 ab f7 97 66 76 15 13 1 Round 1: 63 cb e7 8c 09 cf 4f 3c 3b a9 82 fb 11 13 d8 2c Round 2: a0 fa fe 17 88 54 2c b1 23 a3 39 39 2a 6c 76 05 ... Round 10: 3d 47 0e 52 77 37 2e 10 1f 7e 0e 20 6a 51 7f a7
In this example, an original key was expanded into a number of round keys using the AES key expansion technique. Every round key is created from the one before it using round constants and operations like XOR, RotWord, and SubWord. These round keys are then used in each round of AES encryption to increase security and prevent cryptographic attacks.
Summary
The AES key expansion method creates an initial key and a collection of round keys, which are needed for AES encryption and decryption. In operations like RotWord, SubWord, and XOR, it makes use of round constants. Security is increased since each round key ensures a unique key for each encryption round. The process improves security and protects against cryptographic attacks with AES encryption.