
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
IDEA - International Data Encryption Algorithm
IDEA stands for International Data Encryption Algorithm. IDEA is a block cipher developed by James Massey and Xuejia Lai and initially specified in 1991. It has a 128-bit key length and works with 64-bit blocks.
It consists of a set of eight identical transformations based on bitwise exclusiveor, addition, and multiplication modules. It is based on a symmetric cipher and uses a relatively weak key design technique, hence the algorithm's security is considerably less than that of DES. IDEA failed to gain much popularity because of its complicated development.
It is an IDEA that, unlike other block cipher algorithms, is being studied by the Swiss corporation Ascom. However, they are unique in that they grant permission for free non-commercial usage of their method, which has resulted in IDEA becoming known as the block cipher algorithm used within the famous encryption for the message character.
How IDEA Works?
IDEA is a block cipher that operates on 64-bit plaintext and a 128-bit key. IDEA, like DES, is reversible, which means that the comparable technique can be used for both encryption and decryption. IDEA requires both diffusion and confusion for encryption.
The 64-bit plaintext is broken into four 16-bit sections (P1-P4). These are inputs for the first round. There are eight such rounds. The key contains 128 bits. In each cycle, six sub-keys are generated from the original key, each of which contains 16 bits.
The first round can use keys K1 through K6, the second round can use keys K7 through K12, and the final round can use keys K13 through K18. The last step requires an output modification that requires four subkeys (K49 to K52).
The final output is the result of the output transformation stage. The blocks C1-C4 are joined to generate the final result.
Rounds in IDEA
There are eight rounds in the IDEA. Each round consists of a series of operations on the four data blocks with six keys. The first round can include keys K1 to K6, the second round can have keys K7 to K12, and the last round can have keys K13 to K18. The final stage involves an output modification that requires four subkeys (K49 to K52).
The final output is the result of the output transformation stage. The final output is formed by linking the blocks C1-C4. Each round has 14 steps, as follows −
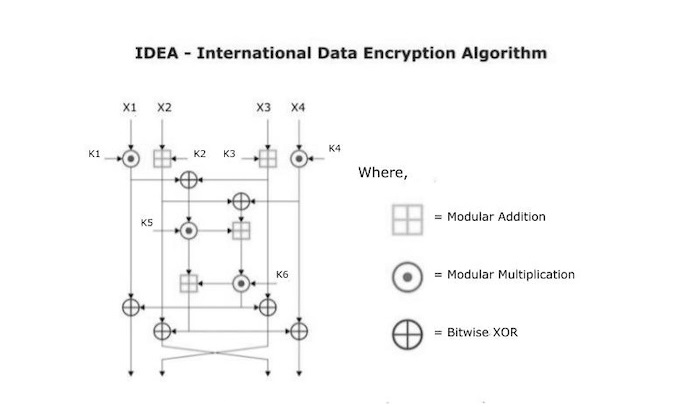
Details of one round in IDEA
Step1 : Multiply * P1 and K1 Step2 : Add * P2and K2 Step3 : Add * P3and K3 Step4 : Multiply * P4 and K4 Step5 : XOR the results of step1 and step3 Step6 : XOR the results of step2 and step4 Step7 : Multiply * the results of step5 with K5 Step8 : Add * the results of step6 and step7 Step9 : Multiply * the results of step8 with K6 Step10 : Add * the results of step7 and step9 Step11 : XOR the results of step1 and step9 Step12 : XOR the results of step3 and step9 Step13 : XOR the results of step2 and step10 Step14 : XOR the results of step4 and step10
The Add * and Multiply * in the next step in each cycle are not elementary addition and multiplication, but rather addition module 216, i.e., 65536, and multiplication module 216 + 1, i.e., 65537.
The common addition gives a number of 17 bits. It can only use 16 bit places for the round2 output.
As a result, it can reduce this number (which is 130753 in decimal) to a 16-bit value. It can take modulo 65536 of this. 130753 modulo 65536 gives 65217, which is 11111111011000001 in binary and is a 16-bit integer that fits well within the system.
The input blocks are P1-P4, the subkeys are K1-K6, and the output of this step is R1-R4 (rather than C1-C4 because this is not the final cipher text). It is an intermediate output that will be handled in the following steps, as well as during the output transformation stage.
Operations used in IDEA
IDEA's operations include −
- IDEA uses bit-by-bit exclusive-OR, denoted as v
- Add integers modulo 216 (modulo 65536), using unsigned 16-bit integers for input and output.
- This operation is referred to as ⊕.
- Integer multiplication modulo 216+1 (modulo 65537), where inputs and outputs are unsigned 16-bit integers. A block of all zeros represents 216. This operation is referred to as ⊗.
Sub-key Generation for a Round
- In the first round, bit positions 1-96 of the key are used. Bits 97-128 remain not used. They are assigned to round two.
- In the second cycle, bits 97-128 are used first, resulting in a 25-bit circular left shift, followed by new bits from 26-89. Bits 90-128 and 1-25 remain unused.
- In the third round, unused bits 90-128 and 1-25 are initially used again, followed by a circular leftshift of 25 bits and the use of bits 51-82. Bit positions 83-128 and 1-50 remain unused.
- In the fourth round, bits 83-128 and 1-50 are used.
- In the fifth round, a circular left-shift of 25 bits arises, with bit positions 76-128 and 1-43 being used. Bits 44-75 remain unused.
- In the sixth round, the unused bit from the fifth round is used, and a left circular shift of 25 bits occurs, leaving bit positions 37-100 empty.
- In the seventh round, the unused bits from the sixth round, 37-100, are used first, followed by a 25-bit circular left shift to bits 126-128 and 1-29. Bits 30-125 remain unused.
- The unused bit location 30-125 from round seven is being used, and the key is deactivated.
Output Transformation
This is a one-time operation. It takes place at the end of the eighth round. As a result, a 64-bit value is separated into four sub-blocks (say R1 through R4), each with its own subkey.
Decryption
Decryption is similar to encryption, but it reverses the order of the round keys and the subkeys for odd rounds. Thus, the inverse of K49-K52 restores the values of subkeys K1-K4 for the respective set operation in cryptography, while K5, and K6 of each group should be restored by K47 and K48 for decryption in this operation in cryptography.
Characteristics of IDEA
The following characteristics of IDEA related to its cryptographic strength −
- Block length − The block length should prevent statistical analysis. However, the complexity of developing an effective encryption algorithm seems to increase exponentially with block size.
- Key strength − The key length should be sufficient to avoid exhaustive key searches. With a length of 128 bits, IDEA appears to be secure in this area well into the future.
- Confusion − The ciphertext should rely on the plaintext and key in a complex and effective manner. The goal is to make it more difficult to determine how the ciphertext statistics relate to the plaintext statistics. IDEA achieves this purpose by three distinct actions, as discussed subsequently. This contrasts with DES, which is based primarily on the XOR operation and small nonlinear S-boxes.
- Diffusion − Each plaintext bit should impact every ciphertext bit, just as each key bit should influence every ciphertext bit. The dispersion of a single plaintext bit over multiple ciphertext bits obscures the plaintext's statistical structure. IDEA is highly effective in this aspect.
Security of IDEA
The IDEA encryption method was thought to be very strong against certain types of attacks, like differential cryptanalysis. Until 2007, no one had successfully found weaknesses in its design. Even the best known attack by that time could only break a simplified version of IDEA with 6 rounds, while the full version uses 8.5 rounds.
Bruce Schneier, a respected cryptographer, praised IDEA in 1996, saying it was the best and most secure encryption method available. However, by 1999, he stopped recommending it because newer, faster methods were developed, some weaknesses were found in IDEA, and there were patent issues.
In 2011, a method called "meet-in-the-middle" was used to break the full 8.5-round IDEA encryption. Then, in 2012, another attack called "narrow-bicliques" was used to weaken IDEA slightly, but it still remains secure for practical use.