
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Blowfish Algorithm
A symmetric-key block cipher called blowfish encryption is frequently used for password hashing, VPNs, and file encryption. Since its introduction in 1993, this encryption method has gained popularity due to its effective encryption and decryption operations. However, more recent, more secure algorithms like AES are gradually taking the place of Blowfish.
Blowfish is a 64-bit block cipher that uses symmetric encryption and a key that can be up to 448 bits long. It was created in 1993 by Bruce Schneier to replace the outdated Data Encryption Standard (DES) and International Data Encryption Algorithm (IDEA) encryption methods.
Though its popularity has decreased recently, blowfish is well known for its ease of use and efficiency. It is being replaced by more recent, stronger encryption methods like the Advanced Encryption Standard (AES).
Features of Blowfish
Some of the main features of the Blowfish algorithm are as follows −
- Block Cipher − Data in Blowfish is encrypted using a block cipher technique using symmetric keys, resulting in 64-bit blocks of encryption.
- Symmetric key algorithm − The Blowfish approach encrypts and decrypts data with the same symmetric encryption key.
- Different length keys − Blowfish offers key lengths ranging from 32 bits to 448 bits. The longer the key, more secure the data. However, processing longer keys usually requires more resources and time.
- Feistel Code − The Feistel cipher development divides the plaintext in half and jumbles each half independently using a sequence of mathematical operations.
Working of Blowfish
An SP network is used by Blowfish; the substitution box (S-box) and permutation box (P-box) must be started first. There are four 32-bit S-boxes with 256 entries each and eight P-arrays with 32-bit subkeys.
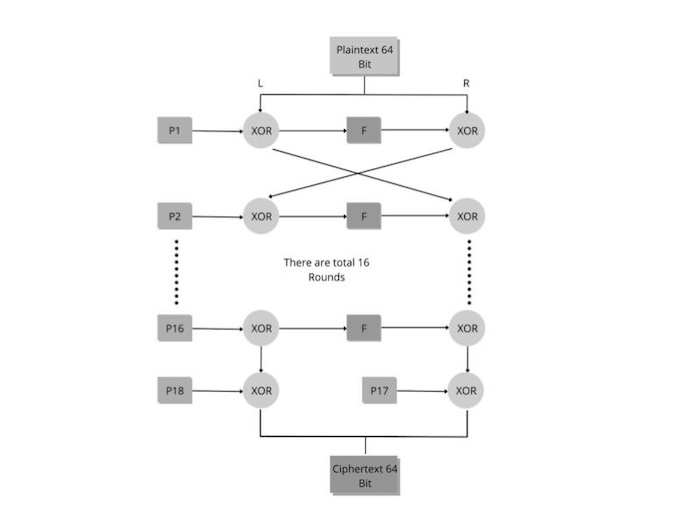
- Step 1 − First, we divided the 64-bit plaintext into two equal blocks, L and R, each containing 32 bits.
- Step 2 − The following actions are taken in each of the 16 encryption cycles that we begin in the following step −
- Now, the L and the first member of the P-array (P1) are XORed.
- Then XOR R with F, where F is a function of L and uses the four blocks that make up the S-box. Below is a summary of function F in entirety.
- The next iteration of the loop starts once L and R are switched.
- Step 3 − L and R are switched again after the loop is completed.
- Step 4 − XOR R with P17 and L with P18 to get the final two unused P-box entries (P17 & P18).
- Step 5: The cipher text is obtained by combining L and R in the final step.
Encryption of Blowfish
A symmetric key block cipher called Blowfish uses the same key for both encryption and decryption of data. Blowfish is quick and efficient mainly because it is simpler than other cryptography methods. While there are a few possible risks involved in achieving the highest level of data security, these risks cannot be ignored.
Here is an in-depth description of the Blowfish encryption technique −
- Key expansion − The initial component that Blowfish uses is a secret key, which can be anything between 32 and 448 bits long. The encryption key is then generated and extended using the P-array and S-boxes precomputation to generate several subkeys.
- Subkeys Generation − The 64-bit blocks that define the stretched-out key are divided into two 32-bit chunks. These components are joined with a few predetermined values to create a new set of subkeys.
- Data Encryption − This is when the exciting part starts. These two 32-bit segments are sixteen times encrypted. Every round involves a challenging set of transpositions and replacements (XOR operations, additions, and lookups in the S-boxes).
- After processing − The 32-bit scrambled bits are reconstructed to form 64-bit ciphertext blocks after 16 rounds.
Decryption of Blowfish
In Blowfish, decryption is carried out by reversing the encryption process. Therefore, everything reverses until the ciphertext is converted back into plaintext.
This Blowfish encryption method uses your private key to protect your data. The best thing about Blowfish is that, if the material is encrypted, it can be challenging to decrypt it without the original key. These technologies from the 1990s are getting a little out of date, however, as more complex and secure encryption methods like AES or Twofish-a substitute for Blowfish-are replacing them.
Example
Suppose that the words "Hi world" will be encrypted using Blowfish. The following are the steps involved −
- The input "Hi world" is initially made up of 64 bits, or 8 bytes, consisting of seven letters plus one space.
- The input consists of 32 bits. The left 32 bits, or "Hi w," are XORed with P1 to produce P1, the product of key expansion.
- Following that, P1 separates the 32 bits into 4 bytes and sends them to each of the four S-boxes using a transformative F-function (F In).
- The third value from the third S-box is XORed with the first two values from the first two S-boxes added to each other.
- 32 bits are produced as the output when this result is added to the fourth S-box's output.
- To create output F1', the output of F In is XORed with the correct 32 bits of the input message, "orld".
- The left half of the message is then replaced with F1', and the right half with P1'.
- For a total of 16 rounds, the same process will be carried out for each of the P-array members that follow.
- The final two elements of the P-array, P17 and P18, are XORed with the outputs P16' and F16' following 16 rounds. After that, they are once again combined to create the input message's 64-bit ciphertext.
Advantages of Blowfish
Blowfish is one of the fastest block ciphers currently in use. It encrypts data using a symmetric encryption key to create ciphertext. Blowfish is still in high demand over thirty years after it was created because it provides the following benefits −
- Considerably less time-consuming and more effective than the DES and IDEA algorithms.
- Unpatented and open to be utilised by anybody, even without authorization.
- Large microprocessors can handle the data encryption process efficiently, even with its intricate initialization step prior to encryption.
- Offers a high level of security for Java-developed programmes and apps.
- Allows for safe user authentication for remote access and secure access for backup tools.
Disadvantages of Blowfish
There are a few disadvantages to using Blowfish for encryption, including the following −
- Changing the key will change the speed.
- It takes a long time to complete the primary routine.
- Due to its short 64-bit block size, the technique is vulnerable to birthday attacks, a kind of brute-force attack.
- Preprocessing for each new key requires 4 KB of text, which slows it down and makes it unusable for various purposes.