
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Hacking RSA Cipher
Hacking the RSA cipher is possible with small prime numbers, but impossible with big numbers. The following aspects explain why it is difficult to break the RSA cipher −
- A brute force approach will fail because there are too many possible keys to sort over. Additionally, this takes a significant amount of time.
- The dictionary attack will not work with the RSA algorithm since the keys are numeric and include no characters.
- The frequency analysis of the characters is difficult to follow because a single encrypted block represents many characters.
- There are no unique mathematical strategies for hacking the RSA cipher.
The RSA decryption equation is −
M = C^d mod n
We can try hacking the RSA cipher using small prime numbers, and the sample code for doing so is provided below −
Hacking using Python
Example
def find_factors(n):
factors = []
for i in range(2, n):
if n % i == 0:
factors.append(i)
return tuple(factors)
def calculate_euler_function(p, q):
return (p - 1) * (q - 1)
def calculate_private_key(e, euler_value):
for i in range(2, euler_value):
if i * e % euler_value == 1:
return i
def decrypt_message(private_key, modulus, ciphertext):
return ciphertext ** private_key % modulus
def main():
e = int(input("Enter value of e: "))
n = int(input("Enter value of n: "))
c = int(input("Enter ciphertext: "))
factors = find_factors(n)
euler_value = calculate_euler_function(factors[0], factors[1])
d = calculate_private_key(e, euler_value)
plain_text = decrypt_message(d, n, c)
print("Decrypted plaintext: ", plain_text)
if __name__ == "__main__":
main()
Run the Code
- Save your Python program.
- Open a terminal or command prompt.
- Navigate to the directory where your code is saved.
Run the script by typing −
python rsa_hacking.py
When you run the program, you will have to enter some values of e, n and ciphertext so after that you will get the plaintext.
Following is the output of the above example −
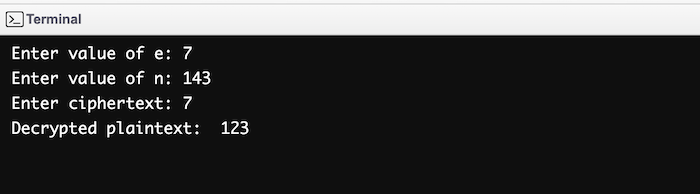
Input/Output
Enter value of e: 7 Enter value of n: 143 Enter ciphertext: 7 Decrypted plaintext: 123
Hacking using Java
So the above code can be written in java also. See the below code for hacking RSA with the help of Java −
Example
import java.util.Scanner;
public class RSAHacking {
public static int[] findFactors(int n) {
int[] factors = new int[2];
for (int i = 2; i < n; i++) {
if (n % i == 0) {
factors[0] = i;
factors[1] = n / i;
break;
}
}
return factors;
}
public static int calculateEulerFunction(int p, int q) {
return (p - 1) * (q - 1);
}
public static int calculatePrivateKey(int e, int eulerValue) {
for (int i = 2; i < eulerValue; i++) {
if ((i * e) % eulerValue == 1) {
return i;
}
}
return -1; // No private key found
}
public static int modPow(int base, int exponent, int modulus) {
int result = 1;
base = base % modulus;
while (exponent > 0) {
if (exponent % 2 == 1) {
result = (result * base) % modulus;
}
exponent = exponent >> 1;
base = (base * base) % modulus;
}
return result;
}
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
System.out.print("Enter value of e: ");
int e = scanner.nextInt();
System.out.print("Enter value of n: ");
int n = scanner.nextInt();
System.out.print("Enter ciphertext: ");
int c = scanner.nextInt();
scanner.close();
int[] factors = findFactors(n);
int eulerValue = calculateEulerFunction(factors[0], factors[1]);
int d = calculatePrivateKey(e, eulerValue);
int plainText = modPow(c, d, n);
System.out.println("Decrypted plaintext: " + plainText);
}
}
Following is the output of the above example −
Input/Output
Enter value of e: 7 Enter value of n: 143 Enter ciphertext: 7 Decrypted plaintext: 123
Hacking Methods
- Brute Force − Trying every possible key until you find the correct one. However, RSA keys are very big, making brute force impractical.
- Factoring − Attempting to divide the modulus (N) into prime factors in order to get the private key. This is challenging with large prime numbers.
- Timing Attacks − Using alterations to the time spent by encryption or decryption processes to access sensitive data.
- Side-channel attacks − These attacks target information leaked by the encryption algorithm's physical implementation, like power consumption or electromagnetic emissions.
- Quantum Computing − In principle, quantum computers can crack RSA encryption more efficiently using algorithms like Shor's algorithm. However, practical quantum computers able to break RSA are currently unavailable.
Summary
Overall, breaking RSA encryption is difficult due to the complexities of factoring large integers. However, researchers are always developing new strategies and technologies to improve encryption systems and secure against attacks in the future.