
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Camellia Encryption Algorithm
Camellia is a symmetric key block cipher that uses a block size of 128 bits and key sizes of 128, 192, and 256 bits. Mitsubishi Electric and Japan's NTT collaborated on its development.
The cipher provides security and processing capabilities comparable to the Advanced Encryption Standard.
The cipher was designed to work with both software and hardware, ranging from low-cost smart cards to high-speed network systems. It is part of the Transport Layer Security (TLS) cryptographic protocol, which is used to secure communications over a computer network like the Internet.
Design of Camellia
Camellia is a Feistel cipher with 18 rounds (128-bit keys) or 24 rounds (192- or 256-bit keys). Every six rounds, a logical transformation layer is applied, known as the "FL-function" or its inverse. Camellia uses four 8x8-bit S-boxes for input and output affine transformations and logical operations.
The cipher additionally uses input and output key whitening. The diffusion layer applies a linear transformation based on a matrix with a branch number of five.
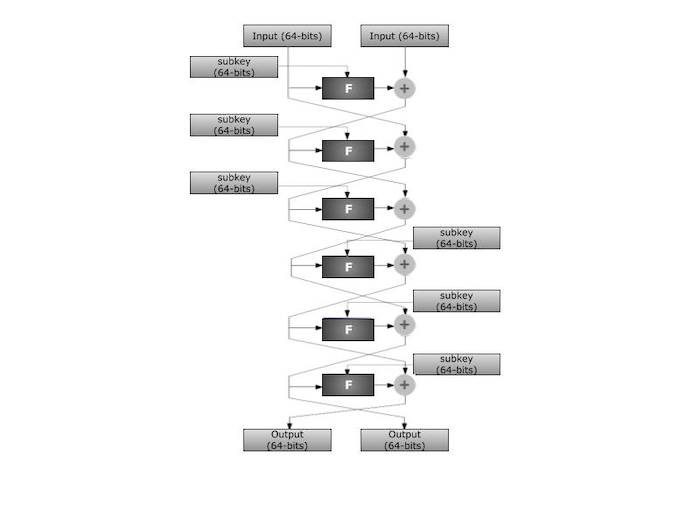
Algorithm
- Camellia is a symmetric block cipher with a secret key length of 128, 192, or 256 bits. The length of plaintext and ciphertext blocks is always 128 bits.
- The following description uses the original names of variables and functions from the Camellia documentation to describe its algorithm.
- The algorithm's most important elements are F-functions. They are used during key encryption and decryption, as well as the creation of helper variables. The F-function accepts 128 input bits, combines them with bits from subkeys ki, and produces 128 new bits. The modification of bits in the F-function is commonly referred to as one round in the algorithm. F-function calls are grouped into blocks. Each block has six rounds.
- Six-round blocks (blocks of six calls to the F-function) are separated by calls to FL-functions and FL-1 functions. They manipulate 64-bit chunks of data and combine them using subkeys kli.
- Both encryption and decryption algorithms are about to repeat the six-round blocks outlined above. The number of repeats is determined by the length of the current secret key.
- For a 128-bit secret key, repeat the 6-round blocks three times. For 192-bit or 256-bit secret keys, repeat the blocks four times.
- In addition, at the start and end of both encryption and decryption methods, data bits are added to bits of subkeys kwi.
- Subkeys, which are used to encrypt or decrypt each data block, are generated in another method. Each block's secret key generates tens of subkeys. They are used in a various operations throughout the main algorithm.
Key schedule
The secret key used in the Camellia cipher can be 128, 192, or 256 bits. Encrypting data blocks needs the creation of a few helper variables, followed by subkeys based on secret key bits. Each subkey is 64 bits long.
To start, calculate two 128-bit variables (KL and KR ) and four 64-bit variables (KLL, KLR, KRL, and KRR). The following equations describe the relationships between those variables −
- KLL equals 64 left bits of KL
- KLR equals 64 right bits of KL
- KRL equals 64 left bits of KR
- KRR equals 64 right bits of KR
The remainder of the connections should be identified using the length of the secret key K.
- for the 128 bit long key: KL equals K and KR equals 0
- for the 192-bit long key: KL equals 128 left bits of K, KRL equals 64 right bits of K and KRR equals ~KRL negation of bits.
- for the 256-bit long key: KL equals 128 left bits of K and KR equals 128 right bits of K
Next, using the preceding helper variables as a basis, two new ones can be calculated: KA and KB. They both have a length of 128 bits. If and only if the secret key has 192 or 256 bits, KB is nonzero. The six help constant values, known as ∑i, should be used while constructing KA and KB.
Finally, one should compute all 64-bit secret subkeys, ki, kwi, and kli, based on four 128-bit long recently created variables, KL, KR, KA, and KB. The Camellia algorithm uses subkeys at every stage of encryption and decryption.
Security of Camellia Encryption
Camellia is known as a cutting-edge, secure cipher. As of now, it is believed hard to break it using a brute-force attack on the keys, not even with the smaller key size option (128 bits). No known successful attacks that significantly break down the cipher have been reported. Comparable to the AES/Rijndael cipher in terms of processing power and security levels is the Japanese cipher.
A block cipher known as Camellia is fully characterised by minimum systems of multivariate polynomials −
- The Camellia (and AES) S-boxes can be defined using a system of 23 quadratic equations in 80 terms.
- The basic schedule can be expressed by 1,120 equations in 768 variables, with 3,328 linear and quadratic terms.
- The full block cipher can be described by 5,104 equations in 2,816 variables, with 14,592 linear and quadratic terms.
- A total of 6,224 equations in 3,584 variables with 17,920 linear and quadratic terms are required.
- The number of free terms is 11,696, which is roughly the same as for AES.
These features will make it possible to break Camellia (and AES) in the future using an algebraic attack, like extended sparse linearisation, if the attack is possible.
Advantages
Here are the advantages of Camellia encryption −
- Camellia encryption is very secure and resistant to a wide range of cryptographic attacks. It has a large key size and a complex circular design, which makes it highly resistant to brute-force attacks.
- Camellia is adaptable and can be used for a variety of cryptographic tasks, like data encryption, digital signatures, and key exchange protocols. Its versatility makes it suitable for a variety of security requirements.
- Despite its excellent security features, Camellia uses relatively few computational resources. It can be efficiently implemented on both software and hardware platforms, making it suitable for a wide range of applications.
- Camellia has been standardised by international organisations like the International Organisation for Standardisation (ISO) and the Internet Engineering Task Force (IETF).
- Camellia is compatible with existing cryptographic infrastructures and protocols, providing easy integration into existing systems without needing significant changes.
Disadvantages
Here are some disadvantages of Camellia −
- Camellia may not be as well-known or widely used as other symmetric-key encryption algorithms, such as AES. This can end up in fewer available resources, libraries, and support than more established algorithms.
- Despite being a common encryption technology, Camellia's use can be limited in some applications and industries. Some businesses can prefer using well-known algorithms, like as AES, because of familiarity as well as trust.
- While Camellia is designed to be secure, no cryptographic approach is free to vulnerabilities. As computational power and cryptographic attacks improve, additional problems in Camellia can be discovered over time, potentially compromising its security.