
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - SHA Algorithm
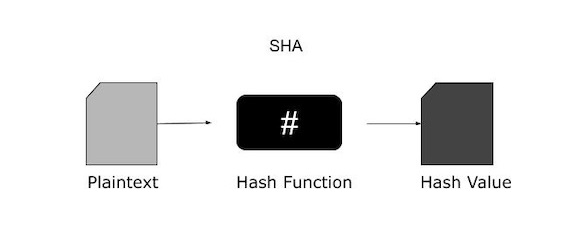
SHA stands for secure hashing algorithm. Data and certificates are hashed using SHA, a modified version of MD5. A hashing algorithm compresses the input data into a smaller, incomprehensible form using bitwise operations, modular additions, and compression functions. You can be asking if hashing can be hacked or decoded. Hashing is one-way, meaning that once data is hashed, a brute force attack is needed to break the resulting hash digest. This is the primary difference between hashing and encryption.
Check out the below image to find out how the SHA algorithm works. Even in the event that a single character changes in the message, SHA is intended to provide a unique hash.
Hashing two similar but distinct messages, like "Heaven" and "heaven is different," is one example. All that differs, however, is one small and one capital letter.
SHAs also help to identify any alterations made to the original message. A user can determine whether a single letter has been altered by comparing the hash digests to the original ones, as they will differ significantly. The deterministic nature of SHA is one of their key features. This means that any computer or user can reproduce the hash digest as long as they know the hash algorithm that was used. One of the reasons that all SSL certificates on the Internet must have been hashed using a SHA-2 method is because of the finite nature of SHAs.
Types of SHA
SHA stands for Secure Hash Algorithm family of cryptographic hash functions. Every SHA type is distinct and comes in a range of numbers. Here are a few common types −
- SHA-1 − This was the first version of SHA. It is currently believed to be less secure as a result of these weaknesses.
- SHA-2 − This includes several hash algorithms with different digest sizes, such as SHA-224, SHA-256, SHA-384, and SHA-512. They are more secure than SHA-1 and are frequently used.
- SHA-3 − The newest member of the SHA family, it was created using different methods than SHA-1 and SHA-2. They include SHA3-224, SHA3-256, SHA3-384, and SHA3-512.
Every kind of SHA generates a unique hash value-a fixed-length character string-from the input data. Among other security-related tasks, these hash values are used in the generation of digital signatures and data integrity verification.
Features of SHA
For cryptography, the Secure Hash Algorithm, or SHA, is useful for several important reasons −
- Data Integrity − SHA generates a fixed-size hash result (often 160, 256, 384, or 512 bits) from input data of arbitrary size. Since a small change in the input data would produce a significantly different hash value, it can be used to verify the integrity of data. If the hash values match, this suggests that the input data has not been altered.
- Uniqueness − SHA tries to produce unique hash results for a range of inputs. While it is still theoretically possible, modern SHA versions (such SHA-256 and SHA-3) are meant to reduce the probability of two different inputs producing the same hash value (a collision).
- Cryptographic Security − Pre-image, second pre-image, collision, and other types of cryptographic attacks are all things that SHA is meant to handle. This means that it will be challenging for an attacker to determine two distinct inputs that result in the same hash value or to reverse-engineer the original input data from its hash value.
- Efficiency − SHA algorithms can produce hash values quickly, even for huge amounts of input data, because they are computationally efficient.
- Wide Use − SHA is widely used in a number of security applications, like blockchain technology, digital signatures, message authentication codes (MACs), and password hashing.
Implementations
So now we will implement SHA Algorithm using Python, Java and C++ −
Implement using Python
So first we will implement SHA using Python's hashlib library to calculate SHA hashes for a given input string. Here the specific version of SHA can be chosen as per your requirement. The code using Python is as follows −
Example
import hashlib
def calculate_sha(input_data):
sha_hash = hashlib.sha256() # Choose different versions sha1(), sha224(), sha384(), etc.
sha_hash.update(input_data.encode('utf-8'))
return sha_hash.hexdigest()
input_data = "Hello, Tutorialspoint!"
sha_hash = calculate_sha(input_data)
print("SHA hash:", sha_hash)
Following is the output of the above example −
Input/Output
SHA hash: caba24f8a70cc24277bffcc27aa952723fbf369f315b9657eebf7c7e42b7a1f9
Implement using Java
Now we will implement SHA using Java's MessageDigest library to calculate SHA hashes for a given input string. The code using Java is given below −
Example
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
public class SHAExample {
public static void main(String[] args) {
String input = "Hello, Everyone!";
try {
MessageDigest shaDigest = MessageDigest.getInstance("SHA-256"); // Choose different versions like "SHA-1", "SHA-224", "SHA-384", etc.
byte[] hashBytes = shaDigest.digest(input.getBytes());
StringBuilder sb = new StringBuilder();
for (byte b : hashBytes) {
sb.append(String.format("%02x", b));
}
String shaHash = sb.toString();
System.out.println("SHA hash: " + shaHash);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
}
}
Following is the output of the above example −
Input/Output
SHA hash: 06b1f0e2138fdb9f0ae8b37cb7a0c77e9e9af1293aa1bfb4d17e57a36542348c
Future of Hashing
SHA-2 is now the industry standard for hashing algorithms, however SHA-3 may someday overtake it. SHA-3 was released in 2015 by the NIST, which also created SHA-1 and SHA-2. Although, it was never accepted as the industry standard for a number of reasons. When SHA-3 was released, most organisations were already switching from SHA-1 to SHA-2, therefore it made no sense to switch to SHA-3 when SHA-2 was still quite secure.
In addition, this is not exactly correct, SHA-3 was seen as being slower than SHA-2. SHA-3 continues to advance with every year, and while it is slower in software, it is faster in hardware when compared to both SHA-1 and SHA-2.
Avelanche Effect
The hash digest for the original message 'Heaven', hashed with SHA-1, is "06b73bd57b3b938786daed820cb9fa4561bf0e8e." The hash digest for the second 'heaven', similar message hashed using SHA-1 looks like this: "66da9f3b8d9d83f34770a14c38276a69433a535b." We call this phenomenon the avalanche effect. This effect is crucial to cryptography since it means that any modification to the input message might significantly change the result. By doing this, attackers will be prevented from deciphering the original meaning of the hash digest and from informing the message's recipient about any modifications made while it was in transit.