
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - SM4 Encryption Algorithm
The SM4 method is the first commercial block cipher algorithm, published by China in 2006 under the name SMS4. The SM4 method is used in the Chinese National Standard for Wireless LAN WAPI (Wired Authentication and Privacy Infrastructure). And the WAPI became China's mandatory national standard.
From the standpoint of security and communication performance, WAPI is an excellent solution for communication infrastructure. This work uses the SM4 algorithm in an Ethernet encryption system.
Structure of SM4
The SM4 algorithm represents a standard Feistel structure. The input, output, and key of the SM4 algorithm are 128 bits. And they are divided into four sections, each of which has 32 bits known as words. The SM4 algorithm consists of 32 identical rounds. The structure for encryption and decryption is the same. The only operations implemented are XOR, circular shifts, and S-box applications. The keys used for decryption are identical to those used for encryption, but in reverse order.
The SM4 method is easily implemented in both software and hardware. It also has a wide range of applications.
A fresh f8 key stream generator that uses SM4 as its fundamental algorithm can be safely used in a 3G communication system. The SM4 algorithm is co-designed in hardware and software in an embedded processor of the MicroBlaze soft core to enable flexibility when designing cryptographic communication equipment. The SMS4 algorithm is also devised and implemented on Java cards.
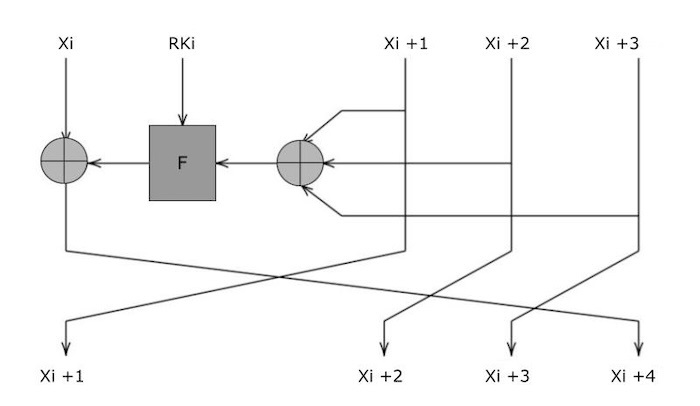
Keys and key parameters
Encryption keys have a length of 128 bits and are expressed as MK=(MK0, MK1, MK2, MK3), where MKi(i=0, 1, 2, 3)} is a 32-bit word. The round keys are represented by (rk0, rk1,...., rk31), with each rki (i=0,..., 31)} representing a word. It is generated using the encryption key and the following parameters −
- FK=(FK0, FK1, FK2, FK3)
- CK=(CK0, CK1,..., CK31)
FKi and CKi are words used to generate the round keys.
Round
Each round is computed based on the four previous round outputs. Xi,Xi+1,Xi+2,Xi+3 Such that −
Xi+4 = Xi⊕ F(Xi+1oplus Xi + 2⊕ Xi + 3⊕ rki), Where F is a substitution function composed of a non-linear transform, the S-box, and linear transform L.
S-box
S-box is fixed for 8-bit input and output, denoted as Sbox(). The S-box, like AES, uses the multiplicative inverse over GF(28). The affine transforms and polynomial bases differ from those of AES, however due to affine isomorphism, they can be calculated quickly using an AES Rijndael S-box.
How it Works?
The SM4 algorithm scrambles data, makes it impossible to understand without a special key. It operates with 128-bit blocks, and the key used to scramble and unscramble the data is also 128 bits. These blocks and keys are divided into four sections, each with 32 bits.
The method scrambles the information by mixing and modifying bits in 32 cycles. This process is the same for scrambling and unscrambling, but the order of the stages varies for unscrambling.
The method only does three things: combine bits using XOR (similar to a digital "either-or" operation), shift them in circles, and use a particular function known as an S-box.
Here are some key terms −
- Words and bytes − They are just terms used to describe clusters of bits.
- S-box − It works similarly to a secret code, converting one set of bits into another.
- Fundamental operations − These are the algorithm's core functions, such as combining and moving bits.
The scrambling key, or MK, is made up of four components. Another type of key, known as round keys, is made from MK and used throughout the scrambling process. These keys help to mix up the bits.
The round function is the algorithm's main component. It scrambles 32 bits at a time, utilising the key for each round.
After scrambling the information, we can reverse the process to unscramble it.
Below is a brief explanation of how it works −
- We begin with plain text (the information we want to protect).
- We divided it into blocks of 128 bits.
- We scramble each block 32 times using the key and several more methods.
- We get scrambled text as output.
- To read the text, we use the same steps but in reverse order.
Example
Consider we have a simple message that we want to encrypt with the SM4 method. The message is "HELLO", and the secret key is "KEY1234567890123". This is how to encrypt it using SM4.
Convert the message and key into binary −
HELLO becomes
| Letter | Binary |
|---|---|
| H | 01001000 |
| E | 01000101 |
| L | 01001100 |
| L | 01001100 |
| O | 01001111 |
KEY1234567890123 becomes
| Letter | Binary |
|---|---|
| K | 01001011 |
| E | 01000101 |
| Y | 01011001 |
| 1 | 00110001 |
| 2 | 00110010 |
| 3 | 00110011 |
| 4 | 00110100 |
| 5 | 00110101 |
| 6 | 00110110 |
| 7 | 00110111 |
| 8 | 00111000 |
| 9 | 00111001 |
| 0 | 00110000 |
| 1 | 00110001 |
| 2 | 00110010 |
| 3 | 00110011 |
Separate the message and key into blocks −
Message blocks (128 bits) −
Block 1: 01001000 01000101 01001100
Block 2: 01001111 (padded with zeros to produce 128 bits)
Each key block contains 128 bits.
- Block 1: 01001011 01000101 01011001 00110001.
- Block 2: 00110010 00110011 00110100 00110101.
- Block 3: 00110110 00110111 00111000 00111001.
- Block 4: 00110000 00110001, 00110010, 00110011.
Encrypt each block − Apply the encryption process to each message block, using the round keys received from the key blocks.
Combine the encrypted blocks − Combine the encrypted blocks to form the final encrypted message.
Send an encrypted message − The encrypted communication is now ready to be transmitted across the network or stored securely.