
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography RSA Algorithm
RSA (Rivest-Shamir-Adleman) is a famous encryption scheme that makes use of a combination of public and private keys. This means you have a non-public key and one that can be shared publicly. Each key can be used to encrypt data, but only the opposite can be decrypted. RSA was evolved in 1977 via MIT researchers Ron Rivest, Adi Shamir and Leonard Adleman, whose name bears the set of ruless call.
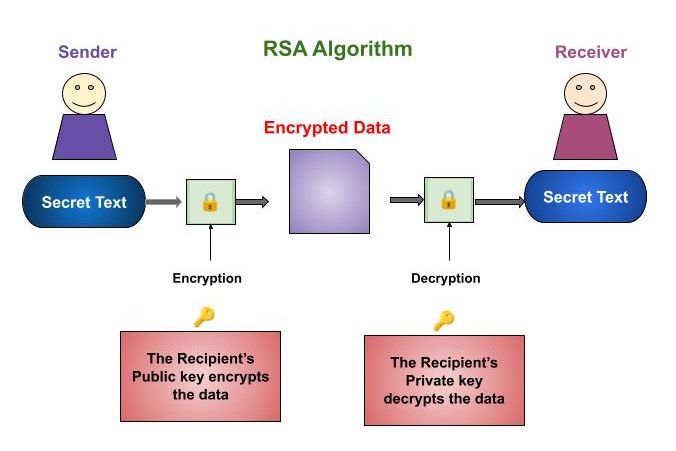
Despite its popularity as a robust encryption method, RSA's high computing demands makes it inefficient and resource-intensive. As a result, it may not be the best choice for encrypting large messages or files because it may drain the system's resources.
How does RSA work?
RSA is based on the problem of breaking down large numbers into their top factors. To create an RSA key pair, you need to pick very big prime numbers, p and q. It is crucial to pick those primes randomly and ensure they are simply unique from each different. The product of p and q, represented as n, becomes the modulus for the public and private keys. While n is publicly known, the values of p and q remain confidential.
The carmecheals' totient function of the product of two primes, p and q, is computed. An integer, e, is chosen as the public exponent. The final step involves calculating d, which serves as the private exponent.
Example
Let's say we choose p = 61 and q = 53.
n = p * q = 61 * 53 = 3233
(n) = (p-1)(q-1) = 60 * 52 = 3120
Let's choose e = 17 (a common choice).
d = 2753 (computed such that (17 * d) mod 3120 = 1)
So, the public key is (3233, 17), and the private key is (3233, 2753).
Encryption
To encrypt a message, the sender Uses the public key (n, e) provided by the recipient. Converts the plaintext message (m) into a ciphertext (c) using the formula −
c = m^e mod n.
Suppose we want to encrypt the message "HELLO". We convert it to ASCII: H(72) E(69) L(76) L(76) O(79).
We will encrypt each ASCII value separately −
- H: C = 72^17 mod 3233 = 2103
- E: C = 69^17 mod 3233 = 2464
- L: C = 76^17 mod 3233 = 2190
- L: C = 76^17 mod 3233 = 2190
- O: C = 79^17 mod 3233 = 875
Decryption
Once the ciphertext (c) is received, the recipient uses their private key (n, d) to decrypt the message. Computes the plaintext message (m) using the formula −
m = c^d mod n.
The recipient receives the ciphertext (2103, 2464, 2190, 2190, 875).
They use their private key to decrypt each value −
- M = 2103^2753 mod 3233 = 72 (H)
- M = 2464^2753 mod 3233 = 69 (E)
- M = 2190^2753 mod 3233 = 76 (L)
- M = 2190^2753 mod 3233 = 76 (L)
- M = 875^2753 mod 3233 = 79 (O)
So, the decrypted message is "HELLO".
Applications and Use Cases
RSA is used for a variety of information security and cryptography applications. Some of the most popular applications include −
Digital Signatures
A digital signature is a technology that allows the recipient of a message to confirm its authenticity, integrity, and non-repudiation. It verifies that the message was not altered in transit.
When creating virtual signatures, the sender first generates a hash cost for the message the usage of a cryptographic hash function. Then you signal it with the help of running the RSA method with the personal key, which produces the digital signature as an output.The recipient can then apply the RSA method to the digital signature with the sender's public key.
You can also verify the signature by comparing it to the hash value created for the message.
Digital Certificates
RSA is commonly used in digital certificates, including SSL certificates. These certificates can be used to authenticate the identification of the people or organizations who run websites.
Digital certificates use RSA to encrypt the certificate issuer's digital signature, which is then confirmed using his public key. The digital certificate contains information like the domain name and the organization that owns the website, which helps establish the website's authenticity to clients.
Secure Key Exchange
Another application of RSA is a secure key exchange between two individuals who have never before shared a secret key. The two parties use the RSA approach to generate a public-private key pair.
The sender creates a symmetric key, encrypts it using the recipient's public key, and transmits the encrypted key to the recipient.
The recipient decrypts it with the private key. Both the sender and the recipient share the same symmetric key, that they can utilize for secure communication.
Secure Communication Protocols
RSA encrypts messages among two parties throughout a community that is not always secure, such as the internet. For example, RSA works with Transport Layer Security (TLS) to installation secure connections among net servers and browsers. Also, RSA allows secure email communication by enabling message encryption and decryption.
It is also utilized in Virtual Private Networks (VPNs). VPNs use TLS to enable a handshake between two parties sharing information. The TLS handshake uses the RSA method to verify the real identities of both parties who participated in the transaction.
How is RSA secure?
RSA's security relies on the difficulty for computers to find the prime numbers in the encryption keys. Longer keys increase the difficulty of code-breaking. While 1024-bit keys were once considered secure, the increasing computing power has led to a shift towards 2048-bit keys.
Elliptic curve cryptography (ECC), an alternative approach to key generation, offers faster speeds and reduced battery usage, making it preferred for mobile devices. A research feat involved creating an RSA key using sound waves, but this method remains impractical for most hackers. Remember, no matter what, every encryption method can be hacked it is just a matter of time and effort.
Advantages of RSA
There are some advantages of Rivest-Shamir-Adleman −
- Enhanced Security − RSA encryption eliminates the need for sharing secret keys, minimizing the risk of unauthorized access.
- Verified Communication Authenticity − The interconnectedness of key pairs ensures only authorized recipients can access messages, preventing interception.
- Efficient Encryption − RSA encryption offers faster encryption compared to the DSA algorithm, speeding up data transfer.
- Data Integrity − Altering data during transmission will disrupt the key usage, preventing unauthorized decryption. This ensures that tampering is detected and the receiver is notified.
Summary
RSA, a popular encryption algorithm since 1977, employs public and private key pairs. While suitable for various tasks, RSA's complexity limits its use for encrypting large data. Instead, RSA excels in creating digital signatures and certificates, ensuring secure authentication, communication, and key exchanges. RSA faces potential vulnerabilities, including unauthorized access, weak key numbers, insecure prime numbers, fault exploitation, and key theft. To mitigate these risks, implementing the recommendations provided in the article is crucial when utilizing RSA for cryptographic applications.