
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - CAST5 Encryption Algorithm
A general process for creating a family of block ciphers is called CAST. Names for individual ciphers include CAST-128 and CAST-256. The CAST cryptography algorithm is the main topic of discussion in this chapter.
What is CAST Ecnryption Algorithm?
Usually used for IP security, the CAST method refers to the Fiestal structure, which divides plain text into equal portions and performs encryption.
- Instead of using DES's 6*4 S-boxes, they use larger 8*32 S-boxes.
- They are made to be used with software.
- Bent functions are used as columns in the CAST S-boxes.
- S-boxes satisfy the avalanche requirement, which states that each bit of input and each bit of round key effects every bit of round output and increases the probability of every given output bit changing by exactly 50%.
What is CAST5?
The most popular CAST cipher is CAST-128, also referred to as CAST5. It is a symmetric key block cipher that is the default cipher for both GPG and PGF versions and is utilized in a variety of products. The developers of it, make it accessible for both commercial and non-commercial use globally at no cost to users.
The CAST5 encryption technique is made to support key sizes ranging from 40 to 128 bits, in increments of 8 bits. This means that the key sizes that can be used are 40, 48, 56, 64,..., 112, 120, and 128 bits.
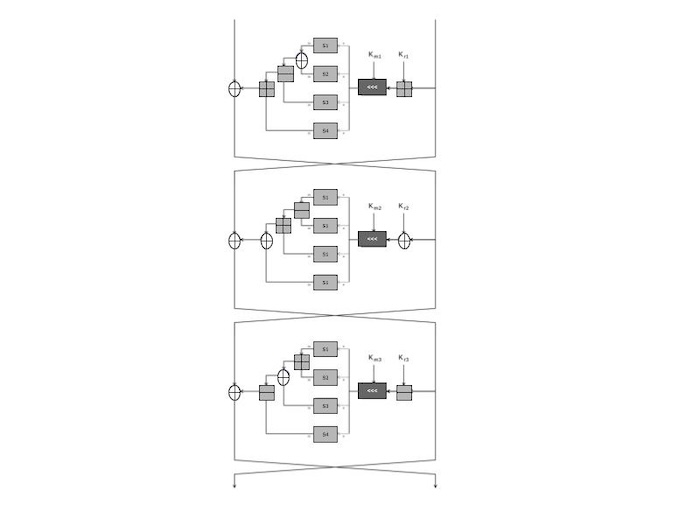
- It is a Feistel Cipher with 16 rounds and 64-bit blocks.
- The range of key sizes is 40 bits to 128 bits.
- Eight 8*32 S-boxes are present. Among these eight boxes, four are utilised for scheduling keys, while the remaining four are used for encryption.
- 37 bits are the round keys.
- The F function divides the output into bytes, XORs the input with 32 bits of round key, and then passes each byte through a separate S-box to get four 32-bit results.
- In different rounds, those are nonlinearly mixed using various combining functions.
- Five more round key bits are used to control the rotation of the output.
Implementation
CAST5 (also known as CAST-128) is a symmetric-key block cipher that encrypts and decrypts data in 64-bit blocks using a 128-bit key.
This implementation ensures the plaintext length is a multiple of 8 bytes by adding padding before encryption. We use the OpenSSL library for C/C++, the pycryptodome library for Python and the Crypto for Java.
Example
The implementation of CAST5 Algorithm using C, C++, Java and Python is as follows −
#include <stdio.h>
#include <string.h>
#include <openssl/aes.h>
void encrypt(const char *plaintext, const unsigned char *key, unsigned char *ciphertext) {
AES_KEY aes_key;
AES_set_encrypt_key(key, 128, &aes_key); // 128-bit AES key
int len = strlen(plaintext);
int padded_len = len + (16 - (len % 16)); // AES block size is 16 bytes
unsigned char padded_text[padded_len];
strcpy((char *)padded_text, plaintext);
memset(padded_text + len, ' ', padded_len - len); // Padding with spaces
for (int i = 0; i < padded_len; i += 16) {
AES_encrypt(padded_text + i, ciphertext + i, &aes_key); // Encrypt each block
}
}
void decrypt(const unsigned char *ciphertext, const unsigned char *key, char *decrypted, int len) {
AES_KEY aes_key;
AES_set_decrypt_key(key, 128, &aes_key); // 128-bit AES key
for (int i = 0; i < len; i += 16) {
AES_decrypt(ciphertext + i, (unsigned char *)decrypted + i, &aes_key); // Decrypt each block
}
decrypted[len] = '\0';
// Remove padding
for (int i = len - 1; i >= 0 && decrypted[i] == ' '; i--) {
decrypted[i] = '\0';
}
}
int main() {
const char *plaintext = "Hello, this is a test message for AES encryption.";
unsigned char key[16] = { 0x01, 0x23, 0x45, 0x67, 0x89, 0xAB, 0xCD, 0xEF,
0x01, 0x23, 0x45, 0x67, 0x89, 0xAB, 0xCD, 0xEF };
int len = strlen(plaintext);
int padded_len = len + (16 - (len % 16));
unsigned char ciphertext[padded_len];
char decrypted[padded_len + 1];
encrypt(plaintext, key, ciphertext);
printf("Encrypted: ");
for (int i = 0; i < padded_len; i++) {
printf("%02x", ciphertext[i]);
}
printf("\n");
decrypt(ciphertext, key, decrypted, padded_len);
printf("Decrypted: %s\n", decrypted);
return 0;
}
Output
The output obtained is as follows −
Encrypted: a0dabfbb3d4ef9bf8f60f25f6f8816814c68655d0b8805b27a5bd74b20a32e5acab9d663d20dcc5a34e7e8ca2fb49d4edaa000197002f4f18c3524701699f26e Decrypted: Hello, this is a test message for AES encryption.
#include <iostream>
#include <cstring>
#include <openssl/aes.h>
void encrypt(const char *plaintext, const unsigned char *key, unsigned char *ciphertext) {
AES_KEY aes_key;
AES_set_encrypt_key(key, 128, &aes_key); // 128-bit AES key
int len = std::strlen(plaintext);
int padded_len = len + (16 - (len % 16)); // AES block size is 16 bytes
unsigned char padded_text[padded_len];
std::strcpy((char *)padded_text, plaintext);
std::memset(padded_text + len, ' ', padded_len - len); // Padding with spaces
for (int i = 0; i < padded_len; i += 16) {
AES_encrypt(padded_text + i, ciphertext + i, &aes_key); // Encrypt each block
}
}
void decrypt(const unsigned char *ciphertext, const unsigned char *key, char *decrypted, int len) {
AES_KEY aes_key;
AES_set_decrypt_key(key, 128, &aes_key); // 128-bit AES key
for (int i = 0; i < len; i += 16) {
AES_decrypt(ciphertext + i, (unsigned char *)decrypted + i, &aes_key); // Decrypt each block
}
decrypted[len] = '\0';
// Remove padding
for (int i = len - 1; i >= 0 && decrypted[i] == ' '; i--) {
decrypted[i] = '\0';
}
}
int main() {
const char *plaintext = "Hello, this is a test message for AES encryption.";
unsigned char key[16] = { 0x01, 0x23, 0x45, 0x67, 0x89, 0xAB, 0xCD, 0xEF,
0x01, 0x23, 0x45, 0x67, 0x89, 0xAB, 0xCD, 0xEF };
int len = std::strlen(plaintext);
int padded_len = len + (16 - (len % 16));
unsigned char ciphertext[padded_len];
char decrypted[padded_len + 1];
encrypt(plaintext, key, ciphertext);
std::cout << "Encrypted: ";
for (int i = 0; i < padded_len; i++) {
std::printf("%02x", ciphertext[i]);
}
std::cout << "\n";
decrypt(ciphertext, key, decrypted, padded_len);
std::cout << "Decrypted: " << decrypted << std::endl;
return 0;
}
Output
The output produced is as follows −
Encrypted: a0dabfbb3d4ef9bf8f60f25f6f8816814c68655d0b8805b27a5bd74b20a32e5acab9d663d20dcc5a34e7e8ca2fb49d4edaa000197002f4f18c3524701699f26e Decrypted: Hello, this is a test message for AES encryption.
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
public class Keypair {
// Method to encrypt the plaintext using AES
public static String encrypt(String plaintext, byte[] key) throws Exception {
// Create a SecretKeySpec from the key
SecretKeySpec secretKey = new SecretKeySpec(key, "AES");
// Create a Cipher instance for AES encryption
Cipher cipher = Cipher.getInstance("AES");
// Initialize the cipher for encryption
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
// Perform encryption
byte[] encryptedBytes = cipher.doFinal(plaintext.getBytes());
// Convert the encrypted bytes to a Base64 encoded string for easy viewing
return Base64.getEncoder().encodeToString(encryptedBytes);
}
// Method to decrypt the ciphertext using AES
public static String decrypt(String ciphertext, byte[] key) throws Exception {
// Create a SecretKeySpec from the key
SecretKeySpec secretKey = new SecretKeySpec(key, "AES");
// Create a Cipher instance for AES decryption
Cipher cipher = Cipher.getInstance("AES");
// Initialize the cipher for decryption
cipher.init(Cipher.DECRYPT_MODE, secretKey);
// Decode the Base64 encoded ciphertext and decrypt it
byte[] decryptedBytes = cipher.doFinal(Base64.getDecoder().decode(ciphertext));
// Return the decrypted string
return new String(decryptedBytes);
}
public static void main(String[] args) {
try {
// The plaintext message to be encrypted
String plaintext = "Hello, this is a test message for AES encryption.";
// 128-bit AES key (16 bytes)
byte[] key = new byte[16];
for (int i = 0; i < 16; i++) {
key[i] = (byte) (0x01 + i);
}
// Encrypt the plaintext
String encrypted = encrypt(plaintext, key);
System.out.println("Encrypted: " + encrypted);
// Decrypt the ciphertext
String decrypted = decrypt(encrypted, key);
System.out.println("Decrypted: " + decrypted);
} catch (Exception e) {
e.printStackTrace();
}
}
}
Output
The output obtained is as shown below −
Encrypted: hPapEiudUO+aenT4/UcgqeMdLte0ZTJbcWkLhu55QE//JsASWBIhUCWrSEolNRbrVjV2epURMZ2kWCvB/glLaw== Decrypted: Hello, this is a test message for AES encryption.
from Crypto.Cipher import CAST
#Encryption function
def encrypt(plaintext, key):
cipher = CAST.new(key, CAST.MODE_ECB)
# Ensure plaintext is a multiple of 8 bytes (64 bits)
if len(plaintext) % 8 != 0:
plaintext += ' ' * (8 - len(plaintext) % 8)
ciphertext = cipher.encrypt(plaintext.encode('utf-8'))
return ciphertext.hex()
#Decryption function
def decrypt(ciphertext, key):
cipher = CAST.new(key, CAST.MODE_ECB)
decrypted = cipher.decrypt(bytes.fromhex(ciphertext))
return decrypted.decode('utf-8').rstrip()
# Plaintext message:
plaintext = "Hello, this is a test message for CAST5 encryption."
key = b'0123456789abcdef' # 16 bytes (128 bits) key
encrypted_text = encrypt(plaintext, key)
print("Encrypted:", encrypted_text)
decrypted_text = decrypt(encrypted_text, key)
print("Decrypted:", decrypted_text)
Output
Following is the output of the above code −
Encrypted: 0b543150504889d797679747bb16d431aab844bfc9e9491dc07bb9a0b019eb18b37dfc9941e4cbce7621c1ccb067fb9743f8743d1aa4842d Decrypted: Hello, this is a test message for CAST5 encryption.
Advantages of CAST5
CAST5 has a number of advantages −
- It is thought that CAST5 is secure. Despite being an older algorithm, there are not many hacks or security breaches. It makes use of a Feistel network structure to increase security.
- For memory usage and computational capability, CAST5 offers a reasonable level of efficiency. Efficient data encryption and decryption make it suitable for scenarios where speed is important.
- CAST5 is not based on any specific hardware or software configuration. It can be used on a range of operating systems and architectures without change because it is implemented in software.
- CAST5 has key sizes ranging from 40 to 128 bits, allowing users to choose the degree of security appropriate for a particular application. By enabling encryption and decryption with a single key, it simplifies key management.
- One can view the details of CAST5 because it is an open algorithm. This makes it trustworthy by allowing the cryptography community to examine and review it with one another.
Disadvantages of CAST5
CAST5 also has some limitations and disadvantages −
- CAST5 supports keys with lengths ranging from 40 to 128 bits. This flexibility allows for different levels of security, however the 40-bit minimum key length is considered to be inadequate for modern cryptographic standards. Longer keys provide more resilience to brute-force attacks.
- CAST5 operates on 64-bit blocks. Even while this was reasonable at the time the method was developed, in comparison to more modern block ciphers with larger block sizes, it is now seen as relatively little. This may lead to security problems, especially when encrypting large volumes of data.
- CAST5 may not provide the same level of security as more current encryption algorithms like AES (Advanced Encryption Standard), even if it has not been compromised in reality. More computer power and advances in cryptography can make older methods more vulnerable to attacks.