
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Electronic Code Book (ECB) Mode
The Electronic Code Book (ECB) is a basic block cipher mode of operation that is mostly used together with symmetric key encryption. It is a simple method for handling a list of message blocks that are listed in sequence.
There are several blocks in the input plaintext. The encryption key is used to independently and individually encrypt each block (ciphertext). Therefore, it is also possible to decrypt each encrypted block individually. Every kind of block can have a different encryption key supported by ECB.
Every plaintext block in ECB has a predefined ciphertext value that matches it, and vice versa. Hence, similar ciphertexts can always be encrypted from identical plaintexts using identical keys. This implies that the output ciphertext blocks will always be the same if plaintext blocks P1, P2, and so forth are encrypted several times using the same key.
In other words, the ciphertext value will always be equal to the plaintext value. This additionally holds true for plaintexts that include somewhat parts that are identical. For example, largely identical ciphertext parts will be included in plaintexts that have identical letter headers and are encrypted using the same key.
Operation
To create the first block of ciphertext, the user takes the first block of plaintext and encrypts it using the key.
He then uses the same procedure and key to go through the second block of plaintext, and so on.
Because the ECB mode is deterministic, the ciphertext blocks that are produced will be identical if plaintext blocks P1, P2,..., and Pm are encrypted twice with the same key.
In reality, we can technically generate a codebook of ciphertexts for every possible block of plaintext for a given key. Then, all that would be required for encryption would be to search for the necessary plaintext and choose the appropriate ciphertext. Because of this, the process is similar to assigning code words in a codebook, which is why it has an official name: Electronic Codebook mode of operation (ECB). Here's a visual representation of it −
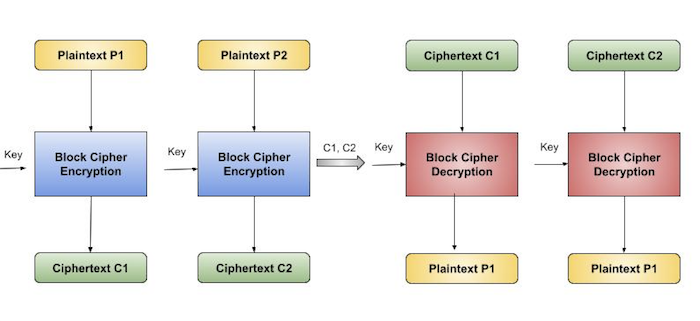
Analysis of ECB Mode
In real life, application data typically contain guessable partial information. For example, one can figure out the salary range. If the plaintext message is contained in a predictable area, an attacker may be able to decipher the ciphertext from ECB by trial and error.
For example, an attacker can retrieve a salary figure after a limited number of attempts if the salary figure is encrypted using a ciphertext from the ECB mode. Since most applications do not wish to use deterministic ciphers, the ECB mode should not be used in them.
Data Encryption Standard vs. Electronic Code Book
IBM created the Data Encryption Standard (DES) in the early 1970s, and in 1977 it was recognised as a Federal Information Processing Standard (FIPS). DES can encrypt data in five different ways. Among these is the original DES mode, or ECB.
FIPS Release 81 now includes three new options: Cipher Block Chaining (CBC), Cipher Feedback (CFB), and Output Feedback (OFB). Later, NIST Special Publication 800-38a was updated to include a fifth mode called Counter Mode. The design concepts of these modes vary, including whether using initialization vectors, whether to use blocks rather than streams, and whether or not encryption faults are likely to spread to subsequent blocks.
Implementation
This implementation performs ECB encryption and decryption using simple byte-level operations. It is important to keep in mind that, in most cases, ECB mode is not secure and needs to be substituted by more secure modes like CBC or GCM.
Example
Below is a simple implementation of ECB mode encryption and decryption in C, C++, Python and Java −
#include <stdio.h>
#include <string.h>
void pad(unsigned char* text, int* text_len, int block_size) {
int padding_length = block_size - (*text_len % block_size);
for (int i = 0; i < padding_length; i++) {
text[*text_len + i] = padding_length;
}
*text_len += padding_length;
}
void unpad(unsigned char* text, int* text_len) {
int padding_length = text[*text_len - 1];
*text_len -= padding_length;
}
void xor_bytes(unsigned char* byte1, unsigned char* byte2, unsigned char* result, int block_size) {
for (int i = 0; i < block_size; i++) {
result[i] = byte1[i] ^ byte2[i];
}
}
void encrypt_ecb(unsigned char* key, unsigned char* plaintext, int plaintext_len, unsigned char* ciphertext, int block_size) {
unsigned char block[block_size];
int num_blocks = (plaintext_len + block_size - 1) / block_size;
int padded_len = plaintext_len;
pad(plaintext, &padded_len, block_size);
for (int i = 0; i < num_blocks; i++) {
memcpy(block, plaintext + i * block_size, block_size);
xor_bytes(block, key, ciphertext + i * block_size, block_size);
}
}
void decrypt_ecb(unsigned char* key, unsigned char* ciphertext, int ciphertext_len, unsigned char* plaintext, int block_size) {
unsigned char block[block_size];
int num_blocks = ciphertext_len / block_size;
for (int i = 0; i < num_blocks; i++) {
memcpy(block, ciphertext + i * block_size, block_size);
xor_bytes(block, key, plaintext + i * block_size, block_size);
}
int plaintext_len = ciphertext_len;
unpad(plaintext, &plaintext_len);
}
int main() {
unsigned char key[] = "ABCDEFGHIJKLMNOP"; // 16 bytes key for AES-128
unsigned char plaintext[] = "Hello, Tutorialspoint!";
int block_size = 16;
unsigned char ciphertext[256];
unsigned char decrypted_plaintext[256];
encrypt_ecb(key, plaintext, strlen((char*)plaintext), ciphertext, block_size);
printf("Ciphertext: ");
for (int i = 0; i < strlen((char*)plaintext) + block_size; i++) {
printf("%02X", ciphertext[i]);
}
printf("\n");
decrypt_ecb(key, ciphertext, strlen((char*)plaintext) + block_size, decrypted_plaintext, block_size);
printf("Decrypted plaintext: %s\n", decrypted_plaintext);
return 0;
}
Output
The output obtained is as follows −
Ciphertext: 09272F282A6A671C3C3E243E242F2323312D2A2A31674D42434041464744455A000000000000000080090000800900008009000080090000800900008009000080090000800900008009000080090000 Decrypted plaintext: Hello, Tutorialspoint! ABCDEFGHCKLGOPKCDOGHCKLGOPKCDOGHCKLGOP
#include <iostream>
#include <cstring>
void pad(unsigned char* text, int* text_len, int block_size) {
int padding_length = block_size - (*text_len % block_size);
for (int i = 0; i < padding_length; i++) {
text[*text_len + i] = padding_length;
}
*text_len += padding_length;
}
void unpad(unsigned char* text, int* text_len) {
int padding_length = text[*text_len - 1];
*text_len -= padding_length;
}
void xor_bytes(unsigned char* byte1, unsigned char* byte2, unsigned char* result, int block_size) {
for (int i = 0; i < block_size; i++) {
result[i] = byte1[i] ^ byte2[i];
}
}
void encrypt_ecb(unsigned char* key, unsigned char* plaintext, int plaintext_len, unsigned char* ciphertext, int block_size) {
unsigned char block[block_size];
int num_blocks = (plaintext_len + block_size - 1) / block_size;
int padded_len = plaintext_len;
pad(plaintext, &padded_len, block_size);
for (int i = 0; i < num_blocks; i++) {
std::memcpy(block, plaintext + i * block_size, block_size);
xor_bytes(block, key, ciphertext + i * block_size, block_size);
}
}
void decrypt_ecb(unsigned char* key, unsigned char* ciphertext, int ciphertext_len, unsigned char* plaintext, int block_size) {
unsigned char block[block_size];
int num_blocks = ciphertext_len / block_size;
for (int i = 0; i < num_blocks; i++) {
std::memcpy(block, ciphertext + i * block_size, block_size);
xor_bytes(block, key, plaintext + i * block_size, block_size);
}
int plaintext_len = ciphertext_len;
unpad(plaintext, &plaintext_len);
}
int main() {
unsigned char key[] = "ABCDEFGHIJKLMNOP"; // 16 bytes key for AES-128
unsigned char plaintext[] = "Hello, Tutorialspoint!";
int block_size = 16;
unsigned char ciphertext[256];
unsigned char decrypted_plaintext[256];
encrypt_ecb(key, plaintext, std::strlen((char*)plaintext), ciphertext, block_size);
std::cout << "Ciphertext: ";
for (int i = 0; i < std::strlen((char*)plaintext) + block_size; i++) {
std::cout << std::hex << (int)ciphertext[i];
}
std::cout << std::endl;
decrypt_ecb(key, ciphertext, std::strlen((char*)plaintext) + block_size, decrypted_plaintext, block_size);
std::cout << "Decrypted plaintext: " << decrypted_plaintext << std::endl;
return 0;
}
Output
The output produced is as follows −
Ciphertext: 9272f282a6a671c3c3e243e242f2323312d2a2a31674d42434041464744455a000000000000000000000000000000000000000000000000 Decrypted plaintext: Hello, Tutorialspoint! ABCDEFGHIJKLMNOPABCDEFGHIJKLMNOPABCDEFGHIJKLMNOP
import java.util.Arrays;
public class ECBEncryption {
public static byte[] pad(byte[] text, int blockSize) {
int paddingLength = blockSize - (text.length % blockSize);
byte[] paddedText = Arrays.copyOf(text, text.length + paddingLength);
for (int i = text.length; i < paddedText.length; i++) {
paddedText[i] = (byte) paddingLength;
}
return paddedText;
}
public static byte[] unpad(byte[] paddedText) {
int paddingLength = paddedText[paddedText.length - 1];
return Arrays.copyOf(paddedText, paddedText.length - paddingLength);
}
public static byte[] xorBytes(byte[] byte1, byte[] byte2) {
byte[] result = new byte[byte1.length];
for (int i = 0; i < byte1.length; i++) {
result[i] = (byte) (byte1[i] ^ byte2[i]);
}
return result;
}
public static byte[] encryptECB(byte[] key, byte[] plaintext) {
int blockSize = key.length;
byte[] paddedPlaintext = pad(plaintext, blockSize);
int numBlocks = paddedPlaintext.length / blockSize;
byte[] cipherText = new byte[paddedPlaintext.length];
for (int i = 0; i < numBlocks; i++) {
byte[] block = Arrays.copyOfRange(paddedPlaintext, i * blockSize, (i + 1) * blockSize);
byte[] encryptedBlock = xorBytes(block, key);
System.arraycopy(encryptedBlock, 0, cipherText, i * blockSize, blockSize);
}
return cipherText;
}
public static byte[] decryptECB(byte[] key, byte[] ciphertext) {
int blockSize = key.length;
int numBlocks = ciphertext.length / blockSize;
byte[] plainText = new byte[ciphertext.length];
for (int i = 0; i < numBlocks; i++) {
byte[] block = Arrays.copyOfRange(ciphertext, i * blockSize, (i + 1) * blockSize);
byte[] decryptedBlock = xorBytes(block, key);
System.arraycopy(decryptedBlock, 0, plainText, i * blockSize, blockSize);
}
return unpad(plainText);
}
public static void main(String[] args) {
byte[] key = "ABCDEFGHIJKLMNOP".getBytes();
byte[] plaintext = "Hello, Tutorialspoint!".getBytes();
byte[] ciphertext = encryptECB(key, plaintext);
System.out.print("Ciphertext: ");
for (byte b : ciphertext) {
System.out.printf("%02X", b);
}
System.out.println();
byte[] decryptedPlaintext = decryptECB(key, ciphertext);
System.out.println("Decrypted plaintext: " + new String(decryptedPlaintext));
}
}
Output
The output obtained is as shown below −
Ciphertext: 09272F282A6A671C3C3E243E242F2323312D2A2A31674D42434041464744455A Decrypted plaintext: Hello, Tutorialspoint!
# ECB encryption & decryption
def pad(text, block_size):
padding_length = block_size - (len(text) % block_size)
padding = bytes([padding_length] * padding_length)
return text + padding
def unpad(padded_text):
padding_length = padded_text[-1]
return padded_text[:-padding_length]
def xor_bytes(byte1, byte2):
return bytes([a ^ b for a, b in zip(byte1, byte2)])
#Encryption Method
def encrypt_ecb(key, plaintext):
block_size = len(key)
padded_plaintext = pad(plaintext, block_size)
num_blocks = len(padded_plaintext) // block_size
cipher_text = b''
for i in range(num_blocks):
block_start = i * block_size
block_end = block_start + block_size
block = padded_plaintext[block_start:block_end]
encrypted_block = xor_bytes(block, key)
cipher_text += encrypted_block
return cipher_text
# Decryption Method
def decrypt_ecb(key, ciphertext):
block_size = len(key)
num_blocks = len(ciphertext) // block_size
plain_text = b''
for i in range(num_blocks):
block_start = i * block_size
block_end = block_start + block_size
block = ciphertext[block_start:block_end]
decrypted_block = xor_bytes(block, key)
plain_text += decrypted_block
return unpad(plain_text)
# key and plaintext
key = b'ABCDEFGHIJKLMNOP' # 16 bytes key for AES-128
plaintext = b'Hello, Tutorialspoint!'
ciphertext = encrypt_ecb(key, plaintext)
print("Ciphertext:", ciphertext)
decrypted_plaintext = decrypt_ecb(key, ciphertext)
print("Decrypted plaintext:", decrypted_plaintext.decode('utf-8'))
Output
Following is the output of the above code −
Ciphertext: b"\t'/(*jg\x1c<>$>$/##1-**1gMBC@AFGDEZ" Decrypted plaintext: Hello, Tutorialspoint!
Drawbacks of ECB Mode
The following are some disadvantages of using ECB Mode −
ECB does not use chaining or an initialization vector; instead, it uses basic substitution. It is simple to implement because of these features. But this is also its biggest weakness. It is cryptologically weak because two identical blocks of plaintext provide two equally identical blocks of ciphertext.
When using identical encryption modes and small block sizes (less than 40 bits), ECB is not recommended. Some words and phrases may appear frequently in the plaintext when block sizes are short. It also means that the same repeating part-blocks of the ciphertext may appear, and that the ciphertext can carry patterns from the same plaintext. When plaintext patterns are easily recognised, hackers have a greater chance of figuring them out and executing a codebook attack.
Even though ECB security is not enough, each block's random pad bits could be added to improve it. Larger blocks (64 bits or more) may have enough entropy, or special characteristics, to prevent a codebook attack.