
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptosystems - Components
A cryptosystem consists of numerous parts that work together to encrypt and protect data. The following are the different parts of a simple cryptosystem −
Plaintext
Encryption Algorithm
Ciphertext
- Key
Symmetric Key
Asymmetric Key
Decryption Algorithm
The collection of all possible decryption keys for a given cryptosystem is called the keyspace.
An interceptor (attacker) is an unauthorized entity that tries to decipher plaintext. He has access to the ciphertext and might be familiar with the decryption formula. But he must never be aware of the decryption key.
Process of Cryptosystem
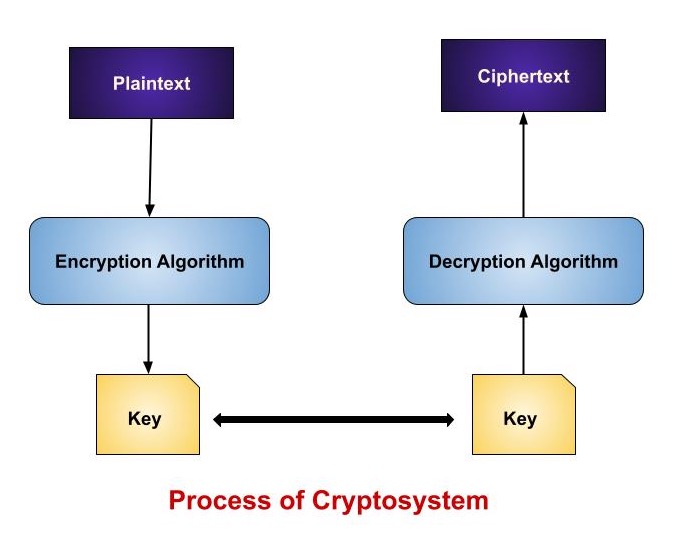
Components
So we will discuss all these components one by one in the below sections −
Plaintext
The original message or data that needs to be kept private while being sent or stored is known as the plaintext.
It can be any kind of information, including text, numbers, and multimedia files.
The plaintext is readable to anyone with access to it prior to encryption, when it is in its original form.
In other words, It is the data to be protected during transmission.
Example: "HELLO, HOW ARE YOU?"
This is the original message that needs to be encrypted.
Encryption Algorithm
It is a mathematical procedure that takes any given plaintext and encryption key and outputs a ciphertext. It is a cryptographic technique that generates ciphertext from plaintext and an encryption key as input.
It works with blocks of data or character sets, according to the algorithm.
The encryption algorithm guarantees the final ciphertext is secure and seems random to unauthorized parties.
Data Encryption Standard (DES), Rivest-Shamir-Adleman (RSA), and Advanced Encryption Standard (AES) are examples of common encryption methods.
Example: Caesar Cipher
In this example, we will use an encryption algorithm called Caesar Cipher. It will shift each character in the given plaintext by a fixed number of positions down the alphabet.
Encryption Algorithm − Shift each letter in the plaintext by 3 positions. So, "H" will become "K", "E" will become "H", and so on.
So the Encrypted Message is: "KHOOR, KRZ DUH BRX?"
Ciphertext
It is the form of the plaintext that has been encoded by the encryption process with a particular encryption key. The ciphertext is not guarded. It flows on public channels. Anyone who has access to the communication channel has the ability to intercept or compromise the message.
It looks as random, unreadable data and cannot be decoded without the proper decryption key.
Ciphertext is sent or kept securely since it has no information about the underlying plaintext.
Example: "KHOOR, KRZ DUH BRX?"
This is the encrypted form of the given plaintext created by the Caesar Cipher algorithm.
Key
A key is a piece of data used by the encryption algorithm to control the encryption and decryption operation.
Keys can be divided into two types: symmetric and asymmetric.
Symmetric Key − Symmetric encryption uses the same key for encryption and decryption. The sender and receiver must have the same private key for encryption and decryption. Symmetric key algorithms are usually fast and efficient, but require a secure key exchange protocol. It's just like having a key to lock and unlock a door.
Asymmetric Key − Asymmetric encryption uses two keys: a public key and a private key. Encryption uses the public key, while decryption uses the private key. It is the same as having a padlock: anyone can lock (encrypt) a message using the public key, but only the owner with the matching key (private key) can decode it.
Example: 3 (for Caesar Cipher algorithm)
The key in our example is the number of positions each letter is shifted in the Caesar Cipher algorithm. In our case, the key is 3.
Both the sender and receiver need to know the key (3) to encrypt and decrypt messages with the help of Caesar Cipher algorithm.
Decryption Algorithm
It is a mathematical procedure that creates a unique plaintext for any given ciphertext and decryption key. It is a cryptographic algorithm that take ciphertext and a decryption key as input and returns plaintext. The decryption algorithm is simply the inverse of the encryption method, and so is closely linked.
It works with the decryption key which is equal to the encryption key used to encrypt the data.
The decryption technique ensures that only authorized people having the correct key can recover the original plaintext.
The decryption algorithm must be secure and efficient in reversing the process of encryption while maintaining data integrity.
Example: Caesar Cipher (with a reverse shift).
To recover the original plaintext from the Caesar Cipher, the decryption algorithm shifts each letter in the ciphertext by the reverse number of positions.
Decryption algorithm: Shift each letter in the ciphertext 3 places in the reverse direction. So, "K" becomes "H", "H" becomes "E", and so on.
Decrypted Message: "Hello, How Are You?"
Summary
Plaintext basic message is "Hello, How Are You?".
The Caesar Cipher encryption algorithm converts the plaintext into the ciphertext as "Khoor, Krz Duh Brx?" use the key (shift of 3) as help.
So above ciphertext is the encrypted form of the given plaintext.
For both encryption and decryption, utilise key (3).
The decryption algorithm (reverse Caesar Cipher) decrypts the ciphertext back into the original plaintext "Hello, How Are You?" using the same key (3).