
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
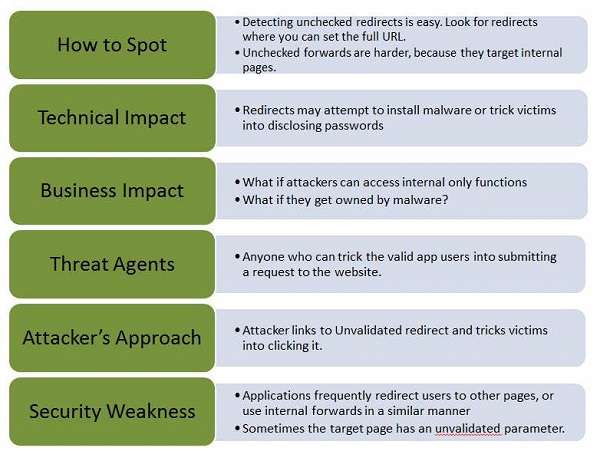
Security Testing - Unvalidated Redirects and Forwards
Most Web applications on net frequently redirect and forward users to other pages or other external websites, however, without validating the credibility of those pages, hackers can redirect victims to phishing or malware sites, or use forwards to access unauthorized pages.
Let us understand Threat Agents, Attack Vectors, Security Weakness, Technical Impact and Business Impacts of this flaw with the help of simple diagram.
Example
Below are some of the classic examples of Unvalidated Redirects and Forwards:
1. Let us say, the application has a page - redirect.jsp which takes a parameter redirectrul. The hacker add an malacious URL that redirects users which performs phishing/installs malware.
http://www.mywebapp.com/redirect.jsp?redirectrul=hacker.com
2. All web application used to forward users to different parts of the site. Inorder to achieve the same, some pages use a parameter to indicate where the user should be redirected if an operation is successful. The attacker crafts an URL that will pass the application's access control check and then forwards the attacker to administrative functionality for which the attacker has not got the access.
http://www.mywebapp.com/checkstatus.jsp?fwd=appadmin.jsp
Preventing Mechanisms
It is better to avoid using redirects and forwards.
If unavoidable then it should be done without involving user parameters in redirecting the destination.
Dev can use the following resources as a guide to prevent this flaw during development process