
- SAP Security - Home
- SAP Security - Overview
- User Authentication & Management
- Network Communication Security
- Protecting Standard Users
- Un-authorizing Logons Protections
- System Authorization Concept
- SAP Security - Unix Platform
- SAP Security - Windows Platform
- SAP Security - Databases
- User Authentication & Single SignOn
- SAP Security - Logon Tickets
SAP Security - Overview
In a SAP Distributed Environment, there is always a need that you protect your critical information and data from unauthorized access. Human Errors, Incorrect Access Provisioning shouldnt allow unauthorized access to any system and there is a need to maintain and review the profile policies and system security policies in your SAP Environment.
To make the system secure, you should have good understanding of user access profiles, password policies, data encryption and authorization methods to be used in the system. You should regularly check SAP System Landscape and monitor all the changes that are made in configuration and access profiles.
The standard super users should be well-protected and user profile parameters and values should be set carefully to meet the system security requirements.
While communicating over a network, you should understand the network topology and network services should be reviewed and enabled after considerable checks. Data over the network should be well protected by using private keys.
Why is Security Required?
To access the information in a distributed environment, there is a possibility that critical information and data is leaked to unauthorized access and system security is broken due to either Lack of password policies, Standard super users are not well maintained, or any other reasons.
A few key reasons of breach of access in a SAP system are as follows −
Strong password policies are not maintained.
Standard users, super user, DB users are not properly maintained and passwords are not changed regularly.
Profile parameters are not correctly defined.
Unsuccessful logon attempts are not monitored and idle user session end policies are not defined.
Network Communication security is not considered while sending data over internet and no use of encryption keys.
Database users are not maintained properly and no security measures are considered while setting up the information database.
Single Sign-ons are not properly configured and maintained in a SAP environment.
To overcome all the above reasons there is a need that you define security policies in your SAP environment. Security parameters should be defined and password policies should be reviewed after regular time intervals.
The Database Security is one of the critical component of securing your SAP environment. So, there is a need that you manage your database users and see to it that passwords are well protected.
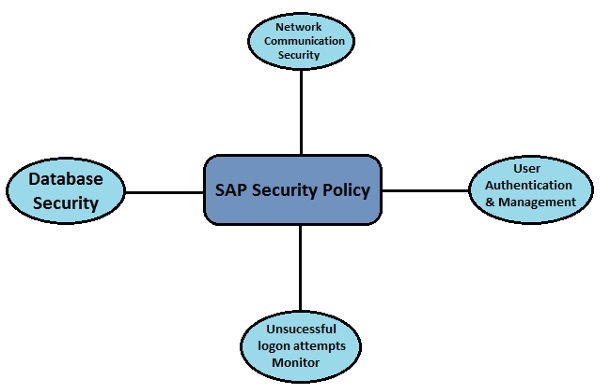
The following Security mechanism should be applied in the system to protect SAP Environment from any unauthorized access −
- User Authentication and Management
- Network Communication Security
- Protecting Standard Users and Super users
- Unsuccessful Logons Protections
- Profile parameters and password policies
- SAP System Security in Unix and Windows Platform
- Single Sign-On Concept
So, the security in SAP system is required in a distributed environment and you need to be sure that your data and processes support your business needs without allowing unauthorized access to critical information. In a SAP system, human errors, negligence, or attempted manipulation on the system can result in loss of critical information.