 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHPPhysics
Chemistry
Biology
Mathematics
English
Economics
Psychology
Social Studies
Fashion Studies
Legal Studies
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What is design space of software-based protocols in computer architecture?
Software-based approaches define a good and competitive concession because they need virtually negligible hardware support and they can lead to a similarly limited number of invalidation failures as the hardware-based protocols. All the software-based protocols depend on compiler support. The design space of software-based protocols is shown in the figure.
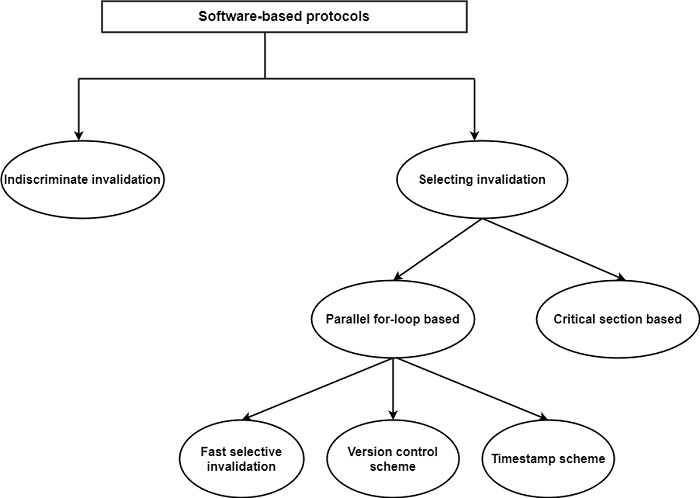
The simplest method is indiscriminate invalidation in which the total cache is invalidated at the end of each programming method. This scheme needs a single hardware structure for passing on or off and invalidating the cache.
Selective invalidation schemes can be classified as per the generation of programs methods −
The critical method scheme depends on the assumption that shared read-write variables are always created in critical methods guarded by software synchronization tools. These variables are discriminating invalidated when the critical method is finished. It can share variables belonging to the similar critical method are located on the similar page and each page is related to a one-time identifier. Loading a cache line will also locate the related one-time identifier in the cache. Invalidation is depended on the one-time identifiers.
There are three parallel for-loop selective invalidation schemes were suggested to remove the disadvantage of indiscriminate invalidation ?−
The fast selective invalidation scheme depends on a write-through cache policy and introduces three instructions to control cache accesses: Memory-Read, CacheRead, and Cache-Invalidate. Cache-Read is used to access a variable when it is approved that the variable is fixed in the cache, alternatively, the Memory-Read command is applied.
An extra bit, known as the change bit, is inserted into each cache line. The Cache-Invalidate command sets all change bits true. An attempt to read a variable with its change bit set true will lead to a read from memory.
The timestamp scheme assigns a clock to each data structure and a timestamp entry to every cache line. The clock related to a data structure is refreshed at the end of each programming method when the data structure was refreshed. The timestamp in the cache directory is set to the value of the corresponding clock+1 when the block is refreshed in the cache.
The same method known as the version control scheme was suggested to prevent unneeded invalidations. The main concept of this technique is that only one process in a program method is allowed to write a variable and this writing creates a new version of the variable. When the writing process exits its program method, the new version develops into the current version which can be utilized by other processors.
First, each processor maintains a counter called the current version number (CVN), for each variable it can use. Second, each cache line is extended with a tag called the birth version number (BVN).
The CVN represents the version of the variable that the processor must use, while the BVN represents a particular version to which the cache copy belongs. A cache miss occurs when the CVN is greater than the BVN otherwise the variable can be accessed from the cache.

