 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHPPhysics
Chemistry
Biology
Mathematics
English
Economics
Psychology
Social Studies
Fashion Studies
Legal Studies
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What is a DNS Name Resolution and explain the cache poisoning attack in DNS?
Let us understand what the domain name system (DNS) is.
Domain Name System
All the web servers connected to the internet have a unique IP address in textual form. Now, the process of translating the textual form into an IP address is called DNS or DOMAIN NAME SERVICE name resolution.
Theoretically during the name resolution process the program that wishes for the name translation contacts a DNS server that returns the translated IP address, but in reality the entire translation may not occur at a single DNS server, rather the DNS server contacted first will recursively call upon other DNS servers to complete the process.
Example
Given below is a diagram of DNS −
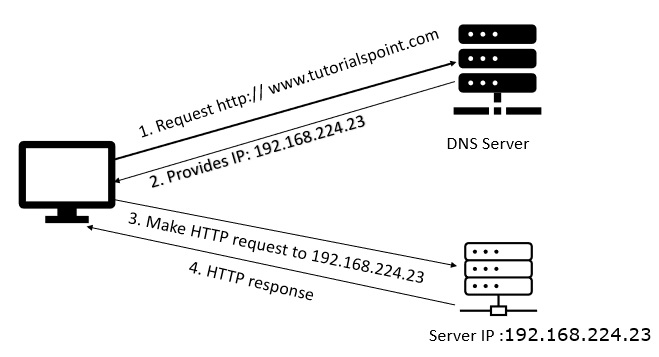
Now let us see about the Cache poisoning attack in DNS.
Cache poisoning attack
The Cache poisoning attack in DNS is explained below in stepwise manner −
Step 1 − It is a form of computer security hacking where incorrect Domain Name System data is fed into the DNS resolver's cache, which results in the name server to return a different IP address.
Step 2 − This results in traffic being diverted to any other computer.
Step 3 − Poisoning attacks on a single DNS server can affect the users serviced directly by the compromised server or those serviced indirectly by its downstream servers.
Step 4 − Generally, a network of computers uses a DNS server provided by computer users or an Internet service provider organization.
Step 5 − DNS servers are used in an organization's network to improve resolution response performance by caching previously obtained resolution results.
Step 6 − To perform a cache poisoning attack, the attacker finds out the loopholes in the DNS software.
Step 7 − A server must correctly validate DNS responses to ensure that they are from an authentic source otherwise the server might end up caching the incorrect entries locally and serve them to other users that make the same request.
Step 8 − This attack can be used to redirect users from a website to another site of the attacker's choice.
Step 9 − For example, an attacker spoofs the IP address DNS entries for a target website on a given DNS server and replaces them with the IP address of a server under their control.
Step 10 − The attacker then creates files on the server under their control with names matching those on the target server.
Step 11 − These files usually contain malicious content, such as computer worms or viruses.
Step 12 − A user whose computer has referenced the poisoned DNS server gets tricked into accepting content coming from a non-authentic server and unknowingly downloads the malicious content.
Step 13 − This technique can also be used for phishing attacks, where a fake version of a genuine website is created to gather personal details such as bank and credit/debit card details.

