 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHPPhysics
Chemistry
Biology
Mathematics
English
Economics
Psychology
Social Studies
Fashion Studies
Legal Studies
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
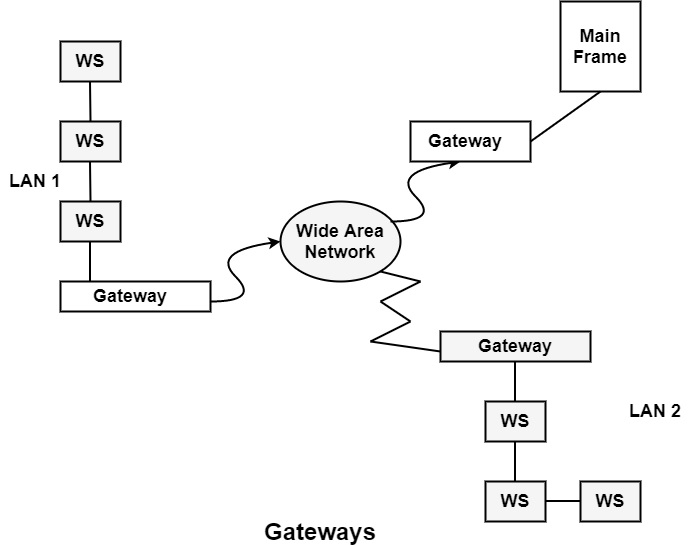
What are the Gateways in Computer Networks?
A device that can bridge multiple network structures is known as a gateway. Therefore gateways can connect two dissimilar LANs. The major difference between gateways and routers is that routers work at the OSI model’s network layer. In contrast, gateways work from the lowest to the topmost layer, i.e., the application layer to the OSI model’s network layer.
Gateways and routers are used correspondingly. It can transform data packets from one protocol architecture to another before forwarding them to connect two multiple networks. Therefore it includes protocol conversion services at the application layer. A gateway is a connecting device that can relate to several networks. They can be implemented at the application layer of the OSI model. They handle messages, locations, and protocol conversion to produce a packet to its terminal among two connections.
The main disadvantage of the gateway is that gateways are moderate because they need to implement intensive conversions.
Given below is an image depicting the structure of gateway in a computer network:−
Characteristics of Gateways
The characteristics of gateways are as follows −
It can provide complete protocol transformation from one proprietary computer network technology to another technology. It means ethernet to token ring or FDDI or some various model or protocol rather than encapsulation.
It requires higher layers of the OSI model, possible by layer 7, the application layer. IBM SNA, DECnet, Internet TCP/IP, and other protocols can be changed from connection to connection.
Unlike bridges and routers, gateways work casually because of protocol conversion. Hence, they can generate bottlenecks of the blockage during the time of peak operation.
Advantages of Gateways
The advantages of gateways are as follows −
It can connect the devices of two several networks having a different design.
It is an intelligent tool with filtering capabilities.
It has control over both collisions and the advertisement area.
It needs a full-duplex mode of connection.
It can make data translation and protocol conversion of the data packet according to the destination network's requirements
It is used to encapsulate and decapsulate the data packets.
It has enhanced security over any other network-related device.

